Platform > Products > Flashpoint automate
Flashpoint Automate
Flashpoint Automate is the low-code automation platform integrated with Flashpoint solutions and numerous other third-party vendors that organizations need to accelerate repeatable security-related processes in order to help detect, analyze, and remediate risk faster.
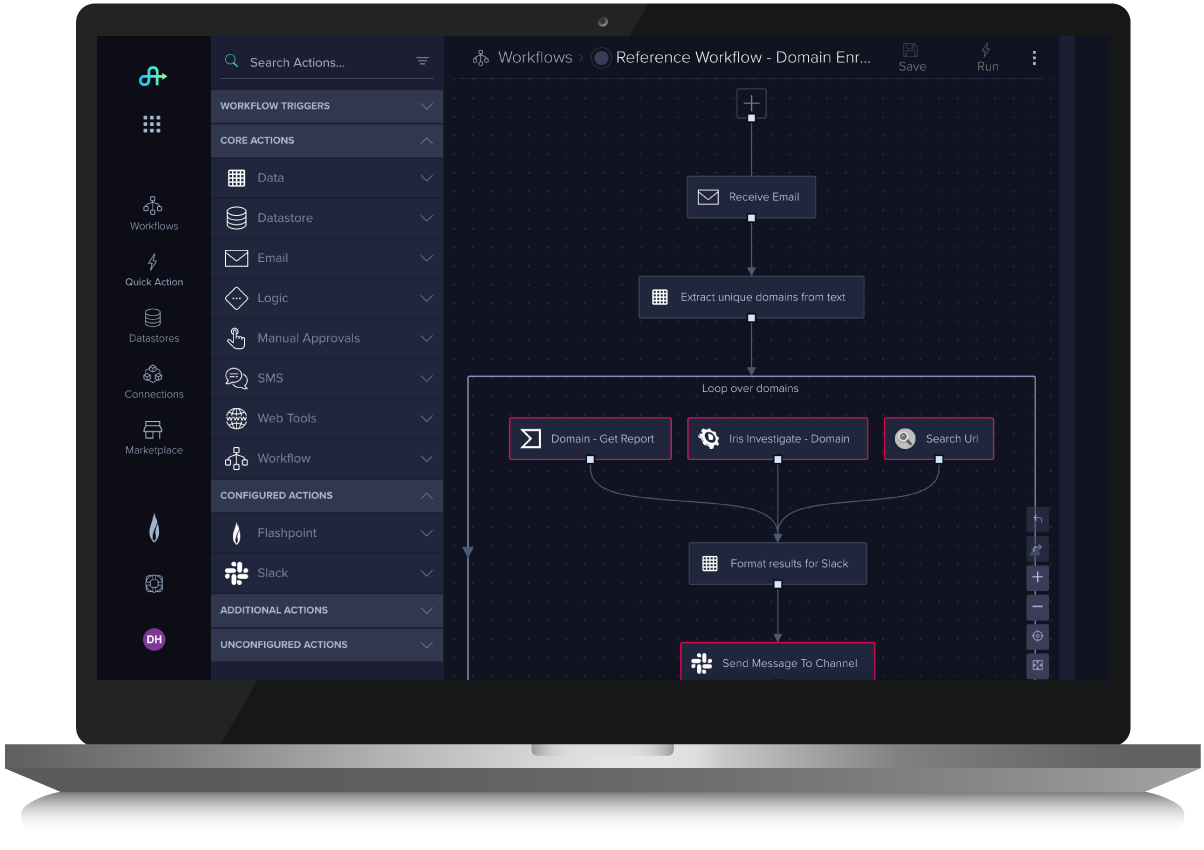
Cyber, fraud, and physical security teams can build and customize automated workflows via drag and drop capabilities in a visual way that represents an overall security related process, which saves time and reduces risk across the organization.

Increase efficiency and save time with automated workflows
Flashpoint Automate’s pre-built reference workflows are designed to help teams get started quickly with common automated workflows. Users have the option to take advantage of out-of-the-box workflows, as well as easily augment them to suit their organization’s internal process.
Align resources to higher priority and complex investigations and responses
Flashpoint Automate enables organizations to avoid repeatable day-to-day work and supports organizations that do not have enough resources to dedicate to the more needle-moving and impactful work that requires teams to stay one-step ahead of threat actors.
Take action based on better informed decisions
Combined with the Flashpoint Intelligence Platform, Flashpoint Automate’s capabilities provide security teams with the additional context needed to ensure they take action on intelligence, prioritize which threats or risks to work on, and remediate those risks from their organization.
Low-code, drag and drop functionality
Utilize a visual canvas with drag-and-drop actions to build workflows and automations, eliminating the need for resources with coding or an engineering background. Users are not required to know how to code, but if they do, there are capabilities within the platform that will allow users to do so.
Integrate directly with Flashpoint’s intelligence platform
The value of Flashpoint’s extensive collections and intelligence combined with Automate’s advanced technology saves organizations time by allowing teams to automate repetitive tasks, acting as the necessary solution security teams need to take action and stop threats.
Continuously growing set of third-party integrations
Integrate with third-party vendors (such as Atlassian Jira, Okta, ServiceNow, Slack, TheHive, VirusTotal, and many others) to help enrich workflows, provide context needed to prioritize, make decisions, and take action. Integrations include commonly used ticketing systems and enrichment sources to help automate investigations and operations workflow.
“Flashpoint has become an integral part of our security infrastructure and threat response workflows, impacting what we do day-in, day-out.”
-Cody Autrey, Texas A&M University, System SecOps Team
