Flashpoint ignite
The Global Leader in Threat Intelligence
Harness the power of Flashpoint’s data, human expertise, and automated analysis. Identify and remediate risk and take rapid, decisive action against cyber threats, fraud, vulnerability, physical, and national security threats.

Gain a Comprehensive
View of Your Organization’s
Threat Landscape
Cyber Threat Intelligence
- Integrate with APIs
- Access finished Intelligence
- Prioritize Vulnerabilities
- Analyze Malware
- Identify Brand Threats
- Detect and Prevent Fraud
- Stop Account Takeover
- Receive Timely Alerts
- Build Threat Actor Profiles
- Analyze Dashboards
- Search with AI
Vulnerability Management
- Access finished Intelligence
- Proritize Vulnerabilities
- Receive Timely Alerts
- Analyze Dashboards
- Integrate With APIs
Physical Security Intelligence
- Access finished Intelligence
- Geolocate Threats
- Produce Open-Source Intelligence (OSINT)
- Search Social Media Data
- Receive Timely Alerts
- Build Threat Actor Profiles
- Analyze Dashboards
- Search with AI
- Monitor Real-Time Events
National Security Intelligence
- Access finished Intelligence
- Proritize Vulnerabilities
- Geolocate Threats
- Produce Open-Source Intelligence (OSINT)
- Search Social Media Data
- Integrate With APIs
- Understand TTPS
- Monitor Real-Time Events
Our Customers Attest to Flashpoint’s Exceptional Value
41B+
Stolen Credentials
5.2B+
Chat Service Messages
138B+
Stolen Accounts
400K+
Vulnerabilities (105K+Pre-CVE)
64M
Paste Site Articles
212M+
Unique Media Assets Collected
1.2B+
Illicit Marketplace Elements
2.1B+
Stolen Credit Cards
Empowering Your Organization to:
Stay Ahead of Evolving Threats
Know Your Vulnerabilities
Protect Your People, Places, and Assets
Inside Flashpoint Ignite
Threat Intelligence Platform
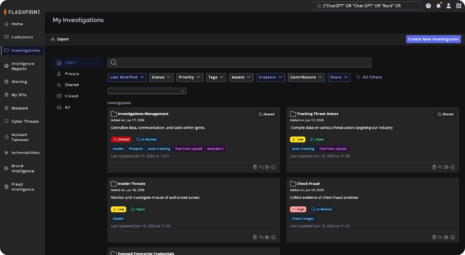
Flashpoint Cyber Threat Intelligence (CTI)
Understand the ‘why’, predict the ‘how’, and stop the ‘now’.
Flashpoint CTI blends automated data collection with expert analysis for a clear view of breach, fraud, identity, technical, and vulnerability threats. It’s intuitive, context-aware, and quick, enabling efficient operations and prompt response to emerging threats.
Flashpoint Physical Security Intelligence (PSI)
Protect people, places, and assets with unmatched situational awareness.
Access geo-enriched data from global social media, messaging apps, defense forums, and illicit communities. Use finished intelligence, analytics tools, and integrated AI to identify, analyze, monitor, and be alerted to critical events, threats, risks, and criminal activity.
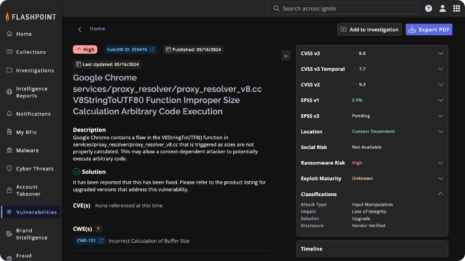
Flashpoint Vulnerability Intelligence
Prioritize and remediate vulnerabilities faster with unparalleled visibility
Identify vulnerabilities about two weeks earlier than NVD by covering zero-day and emerging threats. Discover the latest vulnerabilities, including over 100,000 missed by the CVE database.
Flashpoint National Security Intelligence (NSI)
Inform strategic decisions with OSINT technology, data, and intelligence
Leverage data, technology, and intelligence services to meet diverse national security needs. Access exclusive datasets, powerful analytics, and expert intelligence to stay ahead of threats, eliminate blind spots, and achieve mission success.
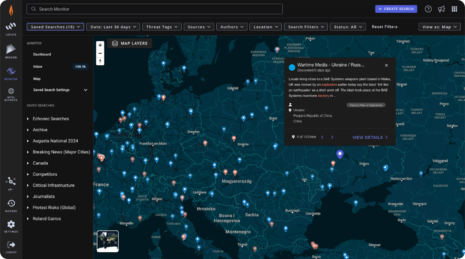
Close the Gap Between Data, Intelligence, and Action
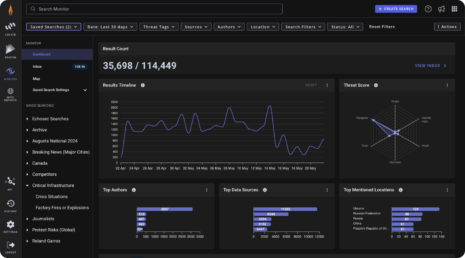
Search Everything
Navigate through more than 3.6 petabytes of text and image data with speed and precision.
Alert on Anything
Receive customized alerts based on your keywords, filters, collection scope, and user roles enabling a quick response.
Access Finished Reports
Augment manual research with meticulously crafted intelligence reports covering technical analysis, geopolitical events, and threat actor assessments.
Gain Insights with Dashboards
Speed up the decision-making process and improve situational awareness with interactive charts, graphs, and maps.
Request Information
Streamline your intelligence cycle by submitting direct requests to Flashpoint analysts for bespoke intelligence and analysis.
Leverage Integrated AI
Enhance speed, efficiency, and understanding with instant summaries and research guidance.
“Flashpoint has given us clear visibility into threat actor techniques, technology, and procedures that we have used to proactively put defenses in place for. It allowed us to disrupt at least one attack campaign that impacted peer financial institutions and included monetary loss.”
VP, Security
Financial Services
Frequently Asked Questions
How does Flashpoint ensure the accuracy and reliability of its threat intelligence?
Flashpoint verifies findings through multiple sources and expert analysis, ensuring accuracy and reliability.
How easy is it to integrate the Ignite Platform with existing security tools?
Ignite is designed for easy integration with your existing security infrastructure. We offer a robust API ecosystem, pre-built integrations with popular SIEM, TIP, and SOAR solutions, and support for industry-standard data formats like STIX and TAXII. View the Flashpoint integrations page for more information.
Can the Ignite Platform be tailored to fit my organization’s specific needs and workflows?
Yes, users can tailor dashboards and workspaces to their priorities, manage user access with granular controls, and set custom alerts for the threats that matter most. Our flexible API framework also allows you to connect Ignite with your unique internal systems and preferred security tools.




