On September 18, a cyber threat actor named “teapotuberhacker” posted on GTAForums.com claiming to have hacked Rockstar Games, the creator of the popular and controversial Grand Theft Auto (GTA) series. In that post, which has since been deleted, teapotuberhacker claimed to have stolen source code for Rockstar’s extremely anticipated Grand Theft Auto VI as well as its predecessor GTA V, in addition to 90 videos of alpha footage.
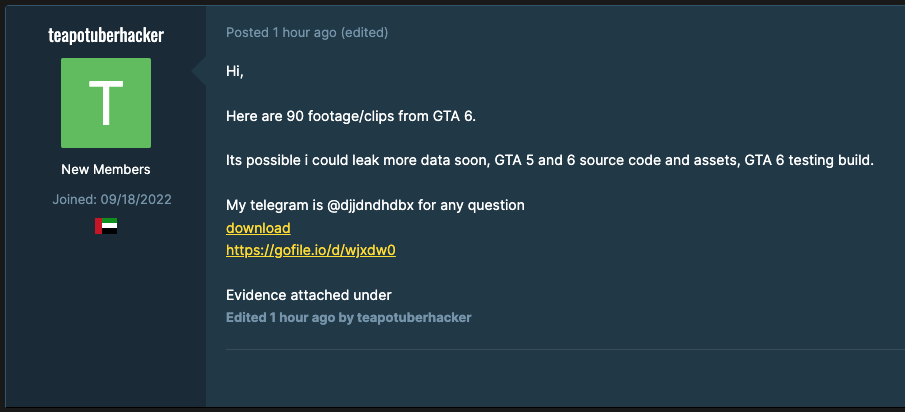
While notable for its scale, this cyberattack also lifted Rockstar Games’ veil of secrecy regarding GTA VI. Over the past nine years, the video game company had been extremely tight-lipped about the game’s development, only officially confirming its existence earlier in February. However, Rockstar Games confirmed the authenticity of the data leak in a public statement:
“We recently suffered a network intrusion in which an unauthorized third party illegally accessed and downloaded confidential information from our systems, including early development footage for the next Grand Theft Auto.”
Rockstar Games
This data breach adds to the growing list of cyberattacks experienced by organizations in the gaming industry. Over the past decade, the video game industry has faced a wide range of cyber threats that range from technical risks to physical security challenges. Exploitable vulnerabilities, cheats, stolen accounts, distributed denial-of-service (DDoS) attacks, and software piracy are the most common. However, in recent years gaming companies have become popular targets for cybercrime gangs and advanced persistent threat (APT) groups.
What we know about the Rockstar data breach
Teapotuberhacker’s original forum thread drew a great deal of attention, eventually making the site inaccessible for some time. Some time later, the forum was cleared of any posts containing stolen content. Out of discontent, teapotuberhacker provided a new Telegram handle as a method of contact. The threat actor then stated they would release a document or PDF containing new information as well as compromised source code on either the 21st or 22nd of September. Flashpoint is currently monitoring for any further activity.
They have not made this timeline. On the day that the original post was made, Flashpoint analysts found that teapotuberhacker’s real world identity had been outed on an online illicit forum. In that thread, titled “The Person Who Hacked GTA 6 and Uber is Arion,” the administrator for that forum claimed that teapotuberhacker was the same individual who had allegedly hacked Microsoft and “owned” Doxbin.
Additionally, the administrator linked teapotuberhacker to other aliases like “White” and “Breachbase, and stated he was a member of LAPSUS$. While the tactics, techniques, and procedures employed by teapotuberhacker are consistent with LAPSUS$, these communities will often make false claims against one another. Flashpoint analysts identified previous doxes where the content may vary on the same individual; these are typically curated by individuals within these communities and should be treated with a healthy degree of skepticism.
Flashpoint has collected numerous other aliases potentially belonging to teapotuberhacker and found that the tactics, techniques, and procedures employed in the Rockstar breach are consistent with other attributed hacks.
Tracking further illicit activity
Flashpoint analysts have been actively monitoring other illicit channels regarding this incident.
While many other users have been posting stolen content derived from teapotuberhacker’s initial drop, we have found additional information potentially detailing how the breach occurred, as well as its scope.
A day before the Rockstar Games breach was disclosed, another threat actor posted in a separate illicit chat channel that they knew teapotuberhacker. Then soon after the drop, this actor disclosed additional context regarding the Rockstar Games breach. To substantiate their claims, they provided multiple screenshots demonstrating teapotuberhacker’s access to Rockstar’s data, as well as images showing their own connection with teapotuberhacker.
The threat actor who claimed to be in touch with teapotuberhacker also claimed the following about the GTA VI data breach. Flashpoint analysts note that this information should only be used as an investigative lead and not interpreted as definitive or conclusive evidence.
- Teapotuberhacker compromised Rockstar Games from an internal Rockstar Slack channel.
- This was done by social engineering a Rockstar employee located in India, gaining access to Rockstar’s Okta.
- Using their access, teapotuberhacker stole source code to GTA V, GTA VI, Red Dead Redemption 2, and Red Dead Redemption 3.
Protect your organization with Flashpoint
Understanding the tactics employed by threat actors and criminal groups helps security teams better protect their networks. Attackers often use tried-and-trued methods, linking together multiple techniques that can be easily replicated against most organizations. To defend against cyber criminals, organizations will greatly benefit from comprehensive and detailed Finished Intelligence. Sign up for a free trial today.


