Blog
BSides Las Vegas 2019 Preview: Visualizing Joker’s Stash
During the past five years, illicit card shops played a crucial role within the fraud ecosystem, enabling hackers to quickly monetize stolen payment card data while providing fraudsters of all skill levels with a means of obtaining that data without having to steal it. Much like the cybercriminal underground, card shops evolve frequently in response to regulatory changes, new technologies, anti-fraud measures, and other external factors.

This blog previews topics that will be discussed during Ian W. Gray and Max Aliapoulios’s upcoming “Giving Credit Where It’s Not Due: Visualizing Joker’s Stash” presentation, which will be held on August 6 at 3 p.m. in the Underground track at BSides Las Vegas.
By Ian W. Gray and Max Aliapoulios
During the past five years, illicit card shops played a crucial role within the fraud ecosystem, enabling hackers to quickly monetize stolen payment card data while providing fraudsters of all skill levels with a means of obtaining that data without having to steal it. Much like the cybercriminal underground, card shops evolve frequently in response to regulatory changes, new technologies, anti-fraud measures, and other external factors.
The rise in 2014 of the prominent card shop Joker’s Stash largely coincided with the U.S. implementation of the EMV payment card standard, which ultimately rendered many fraudsters’ tried-and-true methods of in-store carding ineffective by requiring merchants to support chip-based smart credit cards. But rather than deterring fraudsters, chip cards have motivated many of them to simply shift their focus from in-store carding to card-not-present (CNP) fraud, which refers to fraudulent schemes that occur largely online.
Although in-store carding remains widespread in the U.S. and other regions where EMV technology has yet to be fully adopted, CNP fraud has quickly and rightfully earned a reputation among fraudsters as a cheaper and easier alternative—especially given the ease with which stolen card data for CNP fraud schemes can be obtained via card shops.
Card-shop activity, however, can be difficult for outsiders to observe, because it is largely housed within the deep and dark web (DDW). Some fraudsters have also begun moving toward blockchain DNS and encrypted chat services, which are often perceived as more secure alternatives, but also present a number of barriers to entry.
Nonetheless, having visibility into card shops, the activities they facilitate, and the threat actors who frequent them can be invaluable for security and fraud teams. Flashpoint’s card-shop dataset and dashboard provide our customers with this visibility, delivering critical details related to compromised cards, including bank identification number (BIN), payment method, service code, tracking information, geolocation, and more.
Common use cases for this data include:
- Identifying compromised accounts and cards
- Determining how card data is being compromised
- Understanding long-term trends shaping the market for stolen card data
- Generating geographic heat maps to visualize where compromises are concentrated
- Supporting law-enforcement investigations
We’ll be covering this topic in greater depth next week during our “Giving Credit Where It’s Not Due: Visualizing Joker’s Stash” presentation at BSides Las Vegas. The presentation will be held on August 6 at 3 p.m. in the Underground track.
To preview of some of the data visualizations we’ll be sharing and discussing during the presentation, here are two examples:
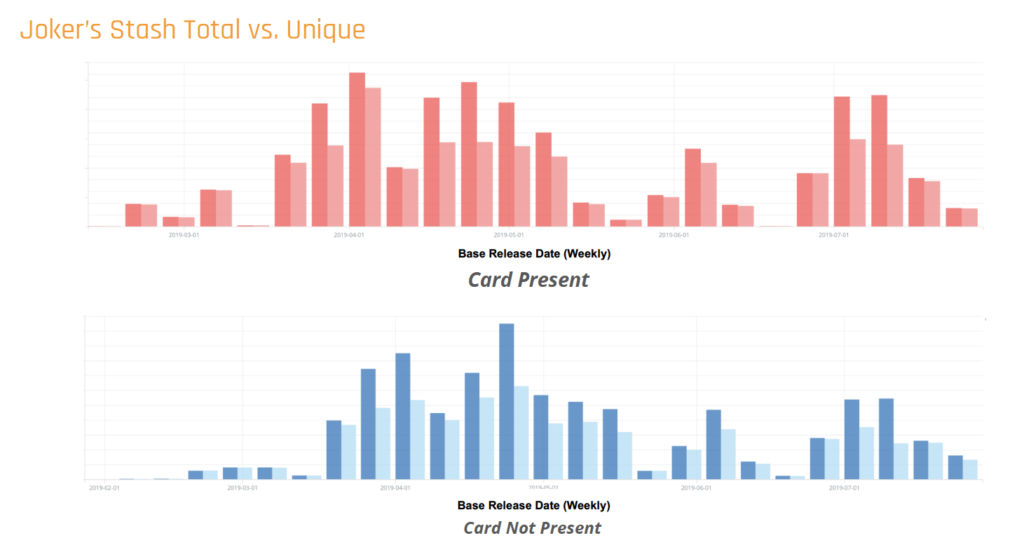
If you won’t be attending BSides Las Vegas but want to learn more about how our card-shop collections and datasets can support your team’s anti-fraud efforts, click here to contact us. We’ll be in touch!

Ian W. Gray
Director of Intelligence, Americas
Ian W. Gray is the director of intelligence for the Americas unit of Flashpoint’s Global Intelligence Team. Ian actively researches and analyzes cybercriminal use of new and emerging technologies for malicious purposes in English and Portuguese-language communities. Additionally, he has been researching policy gaps that contribute to various forms of fraud, as well as the economic factors contributing to cybercrime. Ian is also an adjunct Professor at Fordham University’s Master of Cybersecurity Program.

Max Aliapoulios
Research Developer
Max Aliapoulios is a research developer at Flashpoint and a PhD student at New York University’s Tandon School of Engineering. Max’s published work spans topics that include ransomware tracking, IPTV piracy, and supply chains within underground cybercriminal marketplaces. He continues to apply academic research principles—such as natural language processing, stylometry, and machine learning—to shed light on cybercrime activity.

