Blog
Highlighting a Growing Trend, Attackers Target Narco Forum ‘Legalizer,’ Publish Leak Site of PII
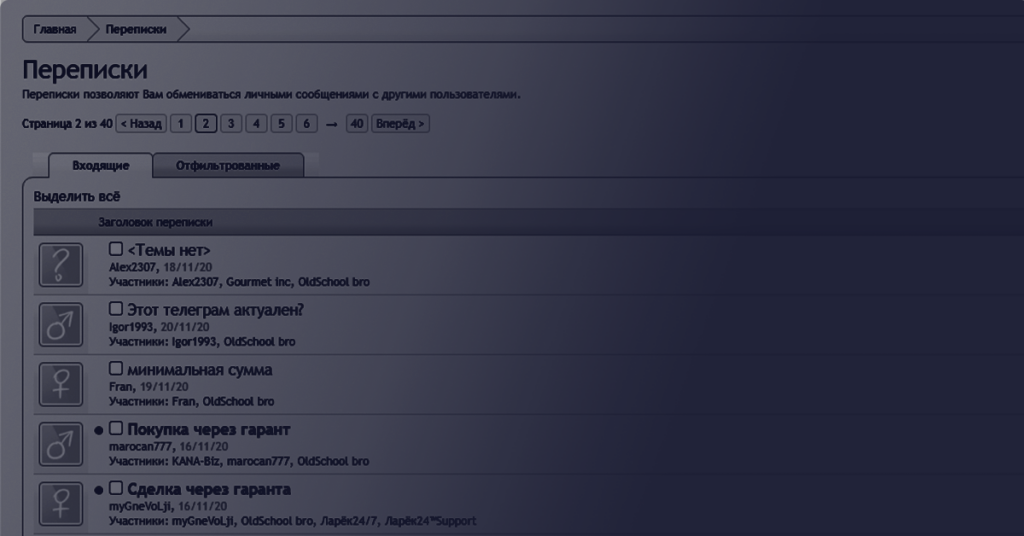
At an unspecified time before August 13, an unknown attacker breached the backup of “Legalizer,” a forum specializing in narcotics trade in the countries of the Russia-led Commonwealth of Independent States (CIS) trade alliance. It is unclear whether the forum itself (pictured below) was also breached, but as of August 30, 2021, it is still operational.
Legalizer hacked
At an unspecified time before August 13, an unknown attacker breached the backup of “Legalizer,” a forum specializing in narcotics trade in the countries of the Russia-led Commonwealth of Independent States (CIS) trade alliance. It is unclear whether the forum itself (pictured below) was also breached, but as of August 30, 2021, it is still operational.
In August the attacker set up a leak site where they displayed personal information of the forum’s administrators and moderators, including the (supposed) passport photo of the wife of one of the administrators, as well as the email addresses and usernames of the site’s users. They indicated that they had not publicized the entirety of the information obtained from the breach and offered to sell the rest for 1 BTC (US$48,000). The breach was later made available on Telegram and the XSS forum. As of this writing, however, it appears that the entirety of the breached database has been made available.
A recent timeline of illicit forum breaches
Flashpoint has observed numerous leaks similar in nature to the Legalizer attack, including the data breaches of Russian cybercrime forums like BHF and Probiv. Though the following timeline is not exhaustive—that list is exclusive to Flashpoint collections—it is intended to highlight major breaches that illustrate a key trend.
Exploit breach
The alleged leak of information from Exploit, rumored to take place in July 2019, shook the trust of users in the forum; some speculated that the leak was the result of the Ukrainian Security Service (SBU) taking over the forum’s infrastructure. As Ukrainian law enforcement officials cooperate with Western law enforcement agencies, users fear possible arrest if they traveled abroad.

Verified breach
In late January 2021, rumors started circulating in several Russian-language illicit forums that the top-tier forum Verified had been breached. Verified is one of the oldest continuously open Russian-language cybercrime forums. On January 21, a user on Raid Forums posted a message claiming that they had acquired the full database of Verified, including user information, private messages, IP addresses, and user contact details, as well as the source code of the forum. The breach was later confirmed, and users were encouraged to update their passwords.
Hydra doxxing
On February 18, a leak site for the Hydra drug market went live, doxing two alleged owners of Hydra. Hydra is a Russian-language Dark Web marketplace and aggregator that has been active since at least 2015. It is currently the largest illicit marketplace in the world—in 2020, the market alone accounted for 75 percent of all dark web market revenue, according to Chainalysis. According to the site, the threat actor running the website had obtained data on the two owners and attempted to blackmail them, but they refused to pay a ransom. As a result, the actor decided to release the data publicly.
Maza breach
On March 3, Flashpoint analysts also detected a breach of the elite cybercrime forum Maza by an unknown threat actor. Flashpoint analysts assess with moderate confidence that the breach is major in scale.
Coordinated attacks?
At this time, Flashpoint analysts do not believe there’s sufficient evidence to suggest that the attacks against the aforementioned forums represent a consolidated effort. Rather, disparate antagonizers are exploiting vulnerabilities in the forums, or hoping to get additional information to leverage against the forum administrators.
As highlighted by Exploit users, the Ukrainian Security Service (SBU) has been extremely active in the last few years—seizing infrastructure from Clop ransomware (Cl0p), arresting members of Egregor ransomware gang, assisting the takedown of Emotet botnet, and aiding countless other cybercrime investigations.
Related Video: Flashpoint & Chainalysis Hydra Illicit Marketplace Webinar: Where the Crypto Money Laundering Trail Goes Dark
How will threat actors respond?
Cybercrime forums exist in anarchy. They are constantly being targeted by competitors, extortionists, law enforcements, and other entities, often anonymously. Threat actors operating in illicit and underground communities have been expressing concern over the pattern of attacks, breaches, and subsequent deanonymization. They are looking for alternatives to traditional registration and operation on cybercrime forums.
While there are discussions around alternative structures invulnerable to deanonymization, no such platform currently exists that provides 100% security. Users have discussed moving away from email as a method of registration, or using two-factor authentication to prevent compromise. RAMP, a recent ransomware-focused upstart, requires prospective users to verify their identities with reputable accounts on top-tier forums.
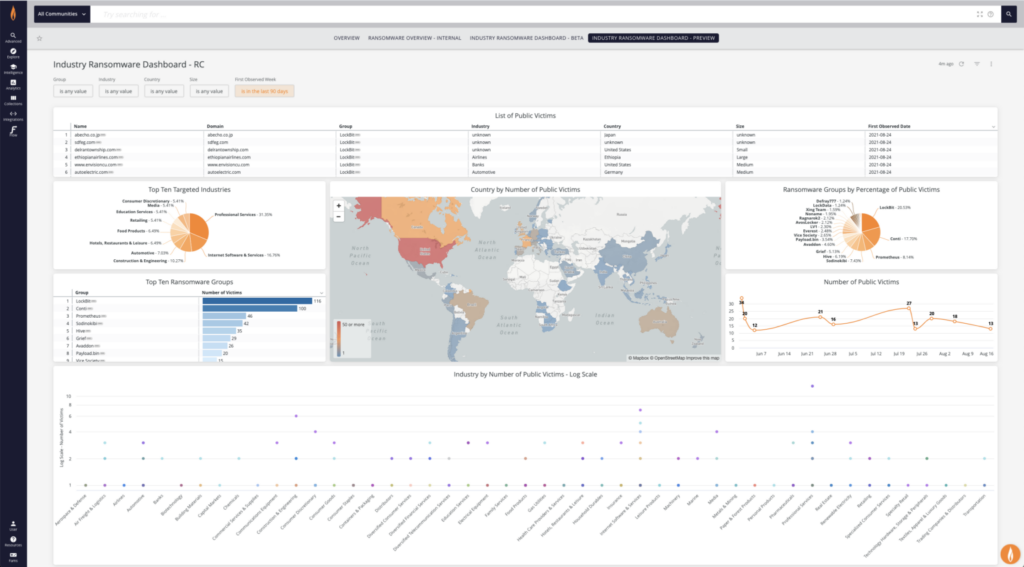
Track Ransomware Activity With Flashpoint
Data and analysis for this article was discovered directly through analyst research in the Flashpoint platform (pictured below). Sign up for a free trial and see firsthand how Flashpoint can help your organization access critical information and insight into ransomware actors and their tactics, techniques and procedures (TTPs).