Blog
After-Action Report: Flashpoint Remediation of 0-Day Exploit on Our Public-Facing Website
Today, researcher Dancho Danchev published a blog post that incorrectly reported that Flashpoint’s public-facing website (flashpoint-intel.com) was “serving malware.”
Flashpoint’s public-facing website is not and was never serving malware. We’re happy to shed light on exactly what happened below.

By Chris Camacho
Today, researcher Dancho Danchev published a blog post that incorrectly reported that Flashpoint’s public-facing website (flashpoint-intel.com) was “serving malware.”
Flashpoint’s public-facing website is not and was never serving malware. We’re happy to shed light on exactly what happened below.
Quick takes:
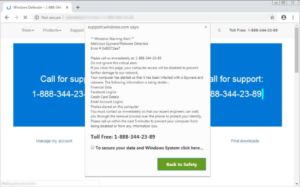
- • The blog post published today references an April 12-13 incident in which flashpoint-intel.com was hit with a 0-day exploit on a specific WordPress plugin.
- • This 0-day exploit caused visitors who had JavaScript enabled to be temporarily redirected to an external website with a pop-up leading to malware.
- • No PII or customer information was breached, and our public-facing website is segregated from all other systems and production environments.
- • The attack wasn’t targeted at Flashpoint specifically. It was an automated attack that picked up our site and injected the vulnerability.
Upon notification of the incident on April 14, Flashpoint security immediately took our public-facing website offline to remediate. The team also notified internal teams to address any inquiries. We also have the technical specifications of the attack which we can share upon request.
When it started / ended:
The earliest confirmed compromised time was April 13 at 01:24 EDT. The last known time the site was not compromised was April 12, 23:43 EDT. Flashpoint assesses with high confidence that flashpoint-intel.com was attacked between April 12th 23:44pm EDT and April 13th 01:24 EDT.
Official remediation efforts started on April 14, 13:42 EDT and the incident was remediated and confirmed by Flashpoint on April 14 at 13:58pm EDT.
Who it affected:
- 1. Anyone who visited the site with JavaScript enabled was redirected
- 2. Anyone who clicked through a pop-up on the redirected site downloaded the malware (downloading the malware did not execute the malware)
Actions we have taken:
- 1. Our security team immediately removed the malicious plugin.
- 2. We have audited all of our plugins and removed any that are not critical to the functionality of our website.
- 3. We increased the frequency of our thorough scanning and auditing procedures to decrease the time from detection to remediation.
- 4. We have written (and tested) custom monitoring that emulates JavaScript and will detect this type of attack in the future.
- 5. Sent a communication to our FPCollab community immediately after notification of the blog post, as well as a direct Flash report to all of our users.
Our security team has hardened our public-facing website and has further web application security improvements scheduled to both improve notification and response times and mitigate these types of attacks in the future.