FLASHPOINT IGNITE » VULNERABILITY INTELLIGENCE
Flashpoint VulnDB
Flashpoint Vulnerability Intelligence (powered by VulnDB) fuses NVD-independent data, real-time exploit analysis, non-CVE visibility, and advanced scoring. Get the speed and insight required to prioritize effectively and diminish the attacker’s advantage.
How Teams Use Flashpoint Vulnerability Intelligence
Intelligence-Led Prioritization
Threat analysts can correlate vulnerability exposure with threat activity and attacker TTPs to pinpoint the highest-risk vulnerabilities.
Seamless Workflow Integration
Vulnerability analysts can deploy vulnerability intelligence with robust integrations and partnerships to ensure quick time to value.
Proactive Software Supply Chain Security
DevSecOps and AppSec teams can support their organizations supply chain security with visibility into affected components, open-source libraries, and dependencies using formats like SBOM.
Strategic Risk Alignment & Reporting
Vulnerability, Threat and Exposure analysts can translate vulnerability exposure into clear executive-level reporting and drive informed investment decisions.
The Intelligence Difference:
Flashpoint vs. The Status Quo
Status Quo
❌ Relying on regurgitated NVD data creates blind spots in OT, hardware, and third-party libraries.
❌ Teams waste time manually correlated basic risk scores created prioritization paralysis.
❌ Traditional systems lack attack context, leading to inaccurate vulnerability prioritization and triage.
❌ The massive volume of new CVEs, combined with the NVD’s slow enrichment process, prevents analysts from conducting effective risk assessments.
❌ Patching is too reactive, it takes months, leaving systems exposed to attacks weaponized within hours.
✅ Adopt NVD-independent intelligence that covers IT, OT, IoT, and supply chain components to eliminate blind spots and provide a single source of truth.
✅ Implement threat-informed risk scoring (like EPSS, Ransomware Likelihood, and Social Risk Scores) to filter noise and focus remediation efforts.
✅ Integrate threat actor TTPs and real-time exploit feeds to validate the true exploitability of a vulnerability, moving beyond theoretical risk scores.
✅ Leverage robust APIs and integrations (SIEM, SOAR, CMDB) to automate data ingestion, correlation, and ticketing, freeing up analyst time.
✅ Continuously map vulnerabilities to your vulnerable attack surface to integrate intelligence and enable early prevention.
The Intelligence Difference:
Flashpoint vs. The Status Quo
Status Quo
❌ Relying on regurgitated NVD data creates blind spots in OT, hardware, and third-party libraries.
❌ Teams waste time manually correlated basic risk scores created prioritization paralysis.
❌ Traditional systems lack attack context, leading to inaccurate vulnerability prioritization and triage.
❌ The massive volume of new CVEs, combined with the NVD’s slow enrichment process, prevents analysts from conducting effective risk assessments.
❌ Patching is too reactive, it takes months, leaving systems exposed to attacks weaponized within hours.
✅ Adopt NVD-independent intelligence that covers IT, OT, IoT, and supply chain components to eliminate blind spots and provide a single source of truth.
✅ Implement threat-informed risk scoring (like EPSS, Ransomware Likelihood, and Social Risk Scores) to filter noise and focus remediation efforts.
✅ Integrate threat actor TTPs and real-time exploit feeds to validate the true exploitability of a vulnerability, moving beyond theoretical risk scores.
✅ Leverage robust APIs and integrations (SIEM, SOAR, CMDB) to automate data ingestion, correlation, and ticketing, freeing up analyst time.
✅ Continuously map vulnerabilities to your vulnerable attack surface to integrate intelligence and enable early prevention.
What Flashpoint’s Vulnerability Intelligence Delivers

“Looking forward to continuing integrating VulnDB information into our processes. The quality of the data is what makes a difference.”
SwisscomUncover Critical Flaws Missed By Public Sources
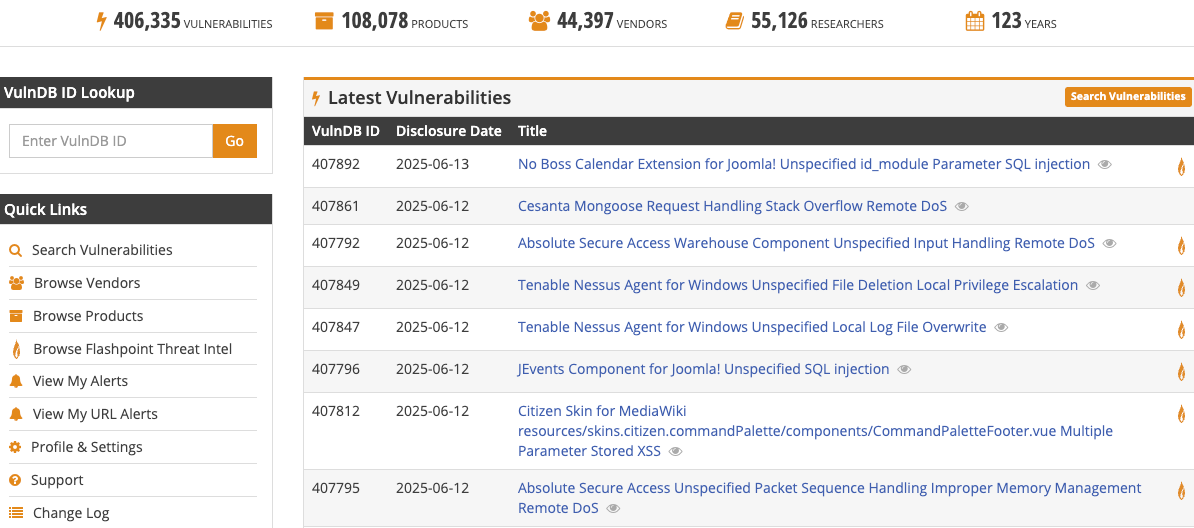
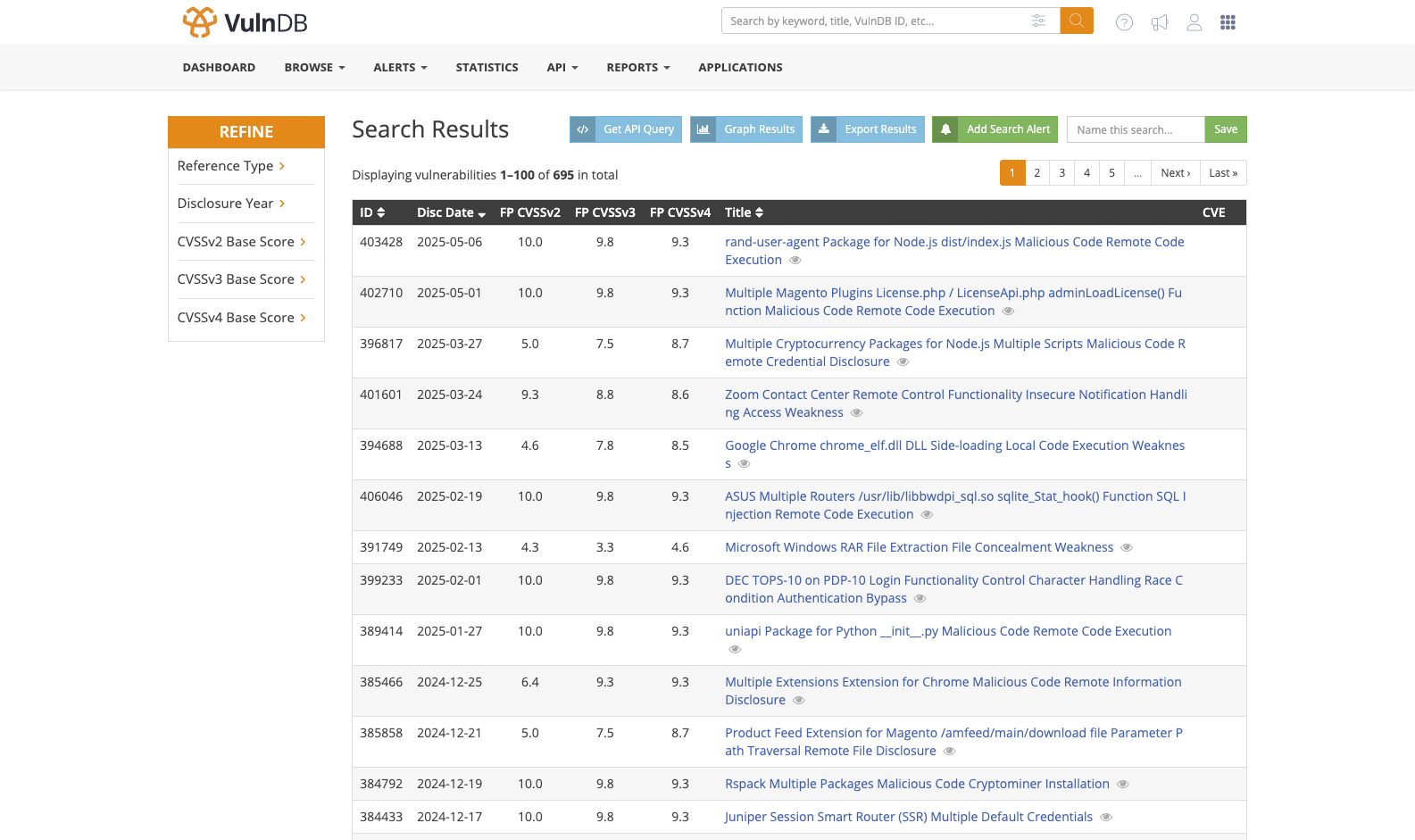
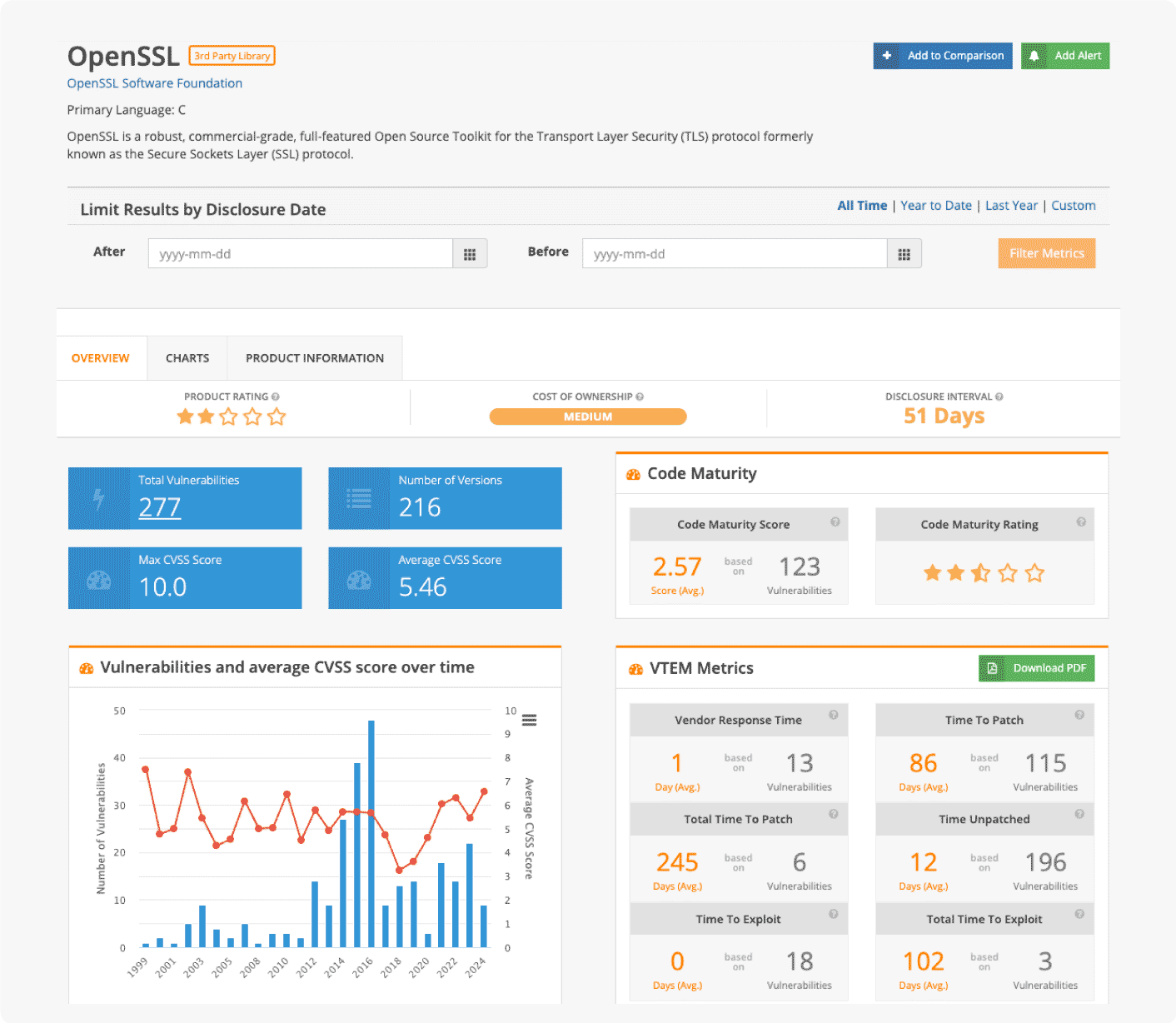
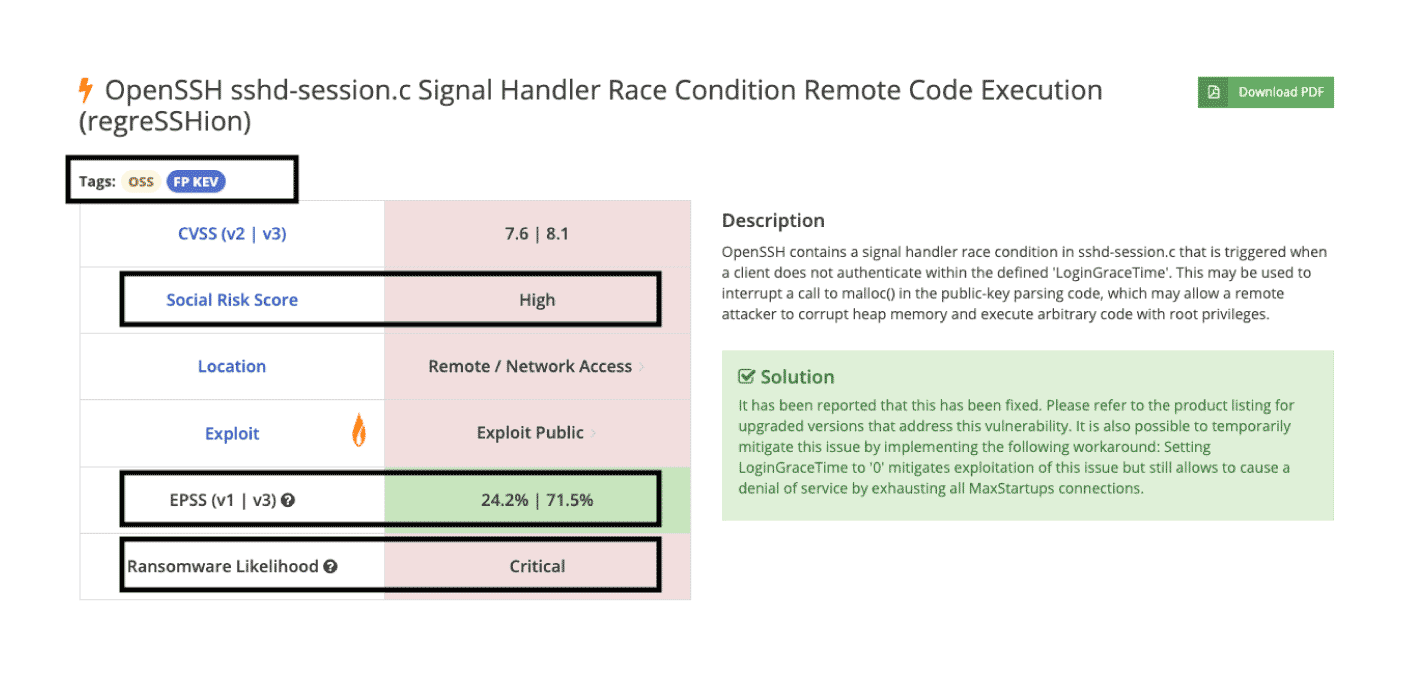
Eliminate dangerous blind spots across your organization with intelligence built on over 415,000 vulnerabilities and rapid time from disclosure to publication (on average 2 weeks faster than NVD). By continuously staying on top of the vulnerability landscape, we deliver comprehensive visibility on vulnerabilities whether they have a CVE ID or don’t.
Does Flashpoint VulnDB include vulnerabilities that are not yet assigned a CVE ID?

Yes, our database includes all CVEs, including 105,000+ not found in NVD and 800+ known exploited vulnerabilities without CVE IDs, ensuring you have full visibility into critical flaws often missed by public sources.
How does Flashpoint’s vulnerability coverage compare to Recorded Future?

Flashpoint excels in comprehensive, deep illicit context, identifying all vulnerabilities and threat actor discussions making it ideal if your primary need is to identify every known vulnerability (public or private) and understand the threat actor chatter around it. Learn more.
Prioritize Risk with Real-Time Exploit Context
Move faster than the adversary. We fuse exploit intelligence, including Ransomware Likelihood and Social Risk Scores, directly into your triage process. This allows you to focus remediation efforts on the critical risks that are actively being exploited, accelerating response time.
How much faster is Flashpoint's intelligence feed than relying solely on the NVD?

Our intelligence is often available days to weeks faster than the NVD. This speed is critical because attackers operate on an hourly, not daily, timeline.

“VulnDB has solved many challenges. For me, our vulnerability intelligence and vulnerability management processes are taken care of. Now it’s on to the next challenge.”
CEO, LINEAS
VulnDB is a critical tool for threat hunters, vulnerability managers, and penetration testers looking to prioritize threat response.
Command Your Proactive Readiness with Threat-Informed Context
Unify your CTI, VM, and AppSec teams around a single, trusted source of truth. We go beyond basic scoring, providing MITRE ATT&CK mapping, exclusive FP KEV tagging and much more, to ensure every customer of Flashpoint Vulnerability Intelligence operates with actionable context and a strategic advantage.
How does Flashpoint support my organization's move toward CTEM?

We provide the crucial vulnerability and threat context needed for the prioritization and validation phases of Continuous Threat Exposure Management (CTEM).
How much context do you provide for each vulnerability?

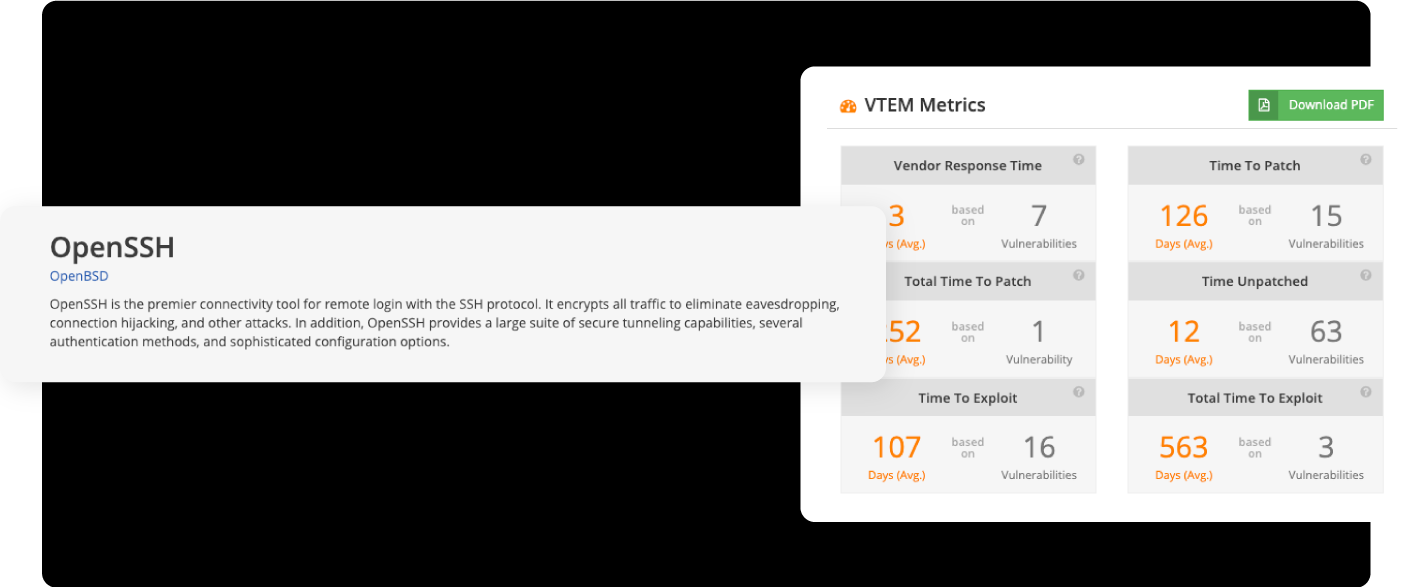
We deliver ~60+ rich data points per vulnerability, including exploit maturity, threat actor chatter, and FP KEV status, to help drive action and triage. This enables lightning-fast detection rule generation and risk-based decision-making.
Analyst Support
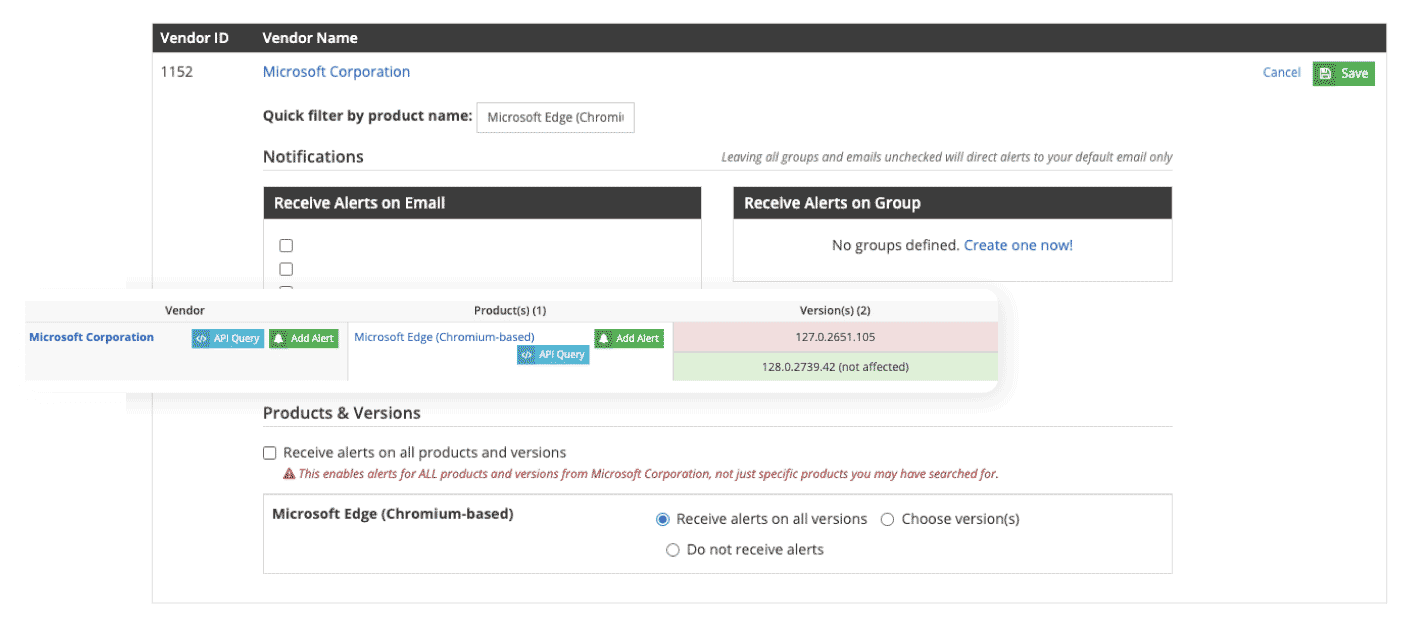
Instantly expand your security skillsets by submitting Requests for Information (RFIs) directly within the platform to access Flashpoint’s world-class intelligence experts. This alleviates strain on internal resources and delivers tailored, deep-dive reports when critical threats emerge.
Is expert analyst support included with Flashpoint?

Absolutely. Direct access to Flashpoint’s analyst team for RFI’s is a core feature in the Vulnerability Intelligence offering, maximizing your team’s effectiveness.

Through the RFI process, Flashpoint intelligence analysts field questions and conduct research inside closed illicit online communities and open sources to provide original, unique analysis.
Additional Offerings to Unify Intelligence for Operational Risk Management
Cyber Threat Intelligence (CTI)
Intelligence links vulnerabilities to broader threat data like TTPs for strategic context and decision-making.
Provides adversary profiles and dark web intelligence to enrich vulnerability context and anticipate attack paths.
Managed and Professional Services
Our services team provides expert support for alerting, incident response, threat actor negotiations, and remediation.
Delivers dedicated analyst support to triage alerts and customize reporting as well as support incident response, threat actor engagements, and strategic readiness planning.
Integrations & APIs
Integrated intelligence drives action, delivering better workflows through robust API access.
Enhances security outcomes by enabling automated data exchange with existing tools for quick time to value and reduced manual effort.
“Looking forward to continuing integrating VulnDB information into our processes. The quality of the data is what makes a difference.”
Swisscom