Blog
OCR, Cybersecurity, and Threat Intelligence: Using Optical Character Recognition and Machine Learning to Identify and Combat Risk
Optical character recognition (OCR) can immediately help security and fraud teams. It adds timely and useful information to their data collections. For example, OCR technology lets CTI and SOC teams find sensitive data in images. This happens when threat actors post that data in hidden online groups across the deep and dark web.

Essential OCR Insights for Cybersecurity Professionals
Optical character recognition (OCR) can immediately help security and fraud teams augment their data collections with timely, actionable intelligence. For example, OCR technology enables CTI and SOC teams to proactively identify when sensitive organizational or customer data—derived from images—is posted by threat actors in illicit communities and actively being leveraged across the deep and dark web.
In this article we:
- Define OCR and look at its history and uses in security.
- Explain how OCR and machine learning save time for threat hunters.
- Describe how criminals use images as proof for their illegal business.
- List real world examples and the value OCR brings to different industries.
What is Optical Character Recognition (OCR)?
OCR technology started over 100 years ago. It began as a way to turn text into sounds for people who could not see. Later, it became a tool for businesses in the 1980s. Today, it has improved a great deal.
Now, OCR is used to pull text and logos out of images. For security teams, it helps find threats to a company. Once a threat is found, the team can take steps to stop it.
Why is Searchable OCR Critical for Modern Fraud Teams?
Machine learning and searchable OCR
Information from OCR should be easy to search right away. This removes the walls between raw data and useful intelligence.
OCR works very well when it is used with machine learning. It is a fast way to check and group images. Advanced OCR can even find text in any direction or language. This allows teams to find fraud in illicit groups and stop risks quickly.
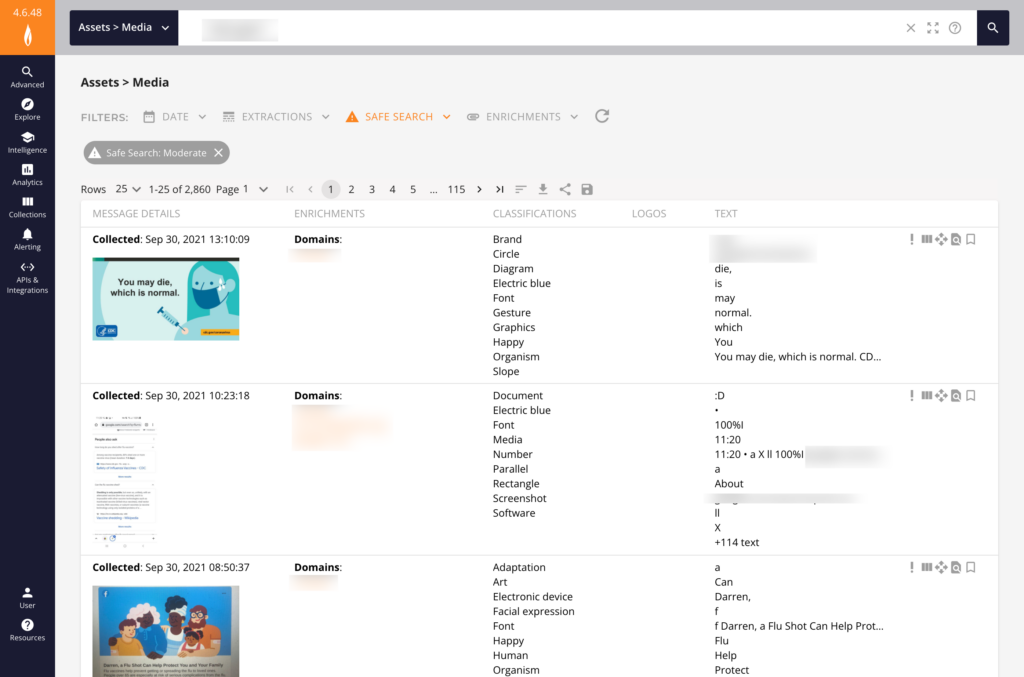
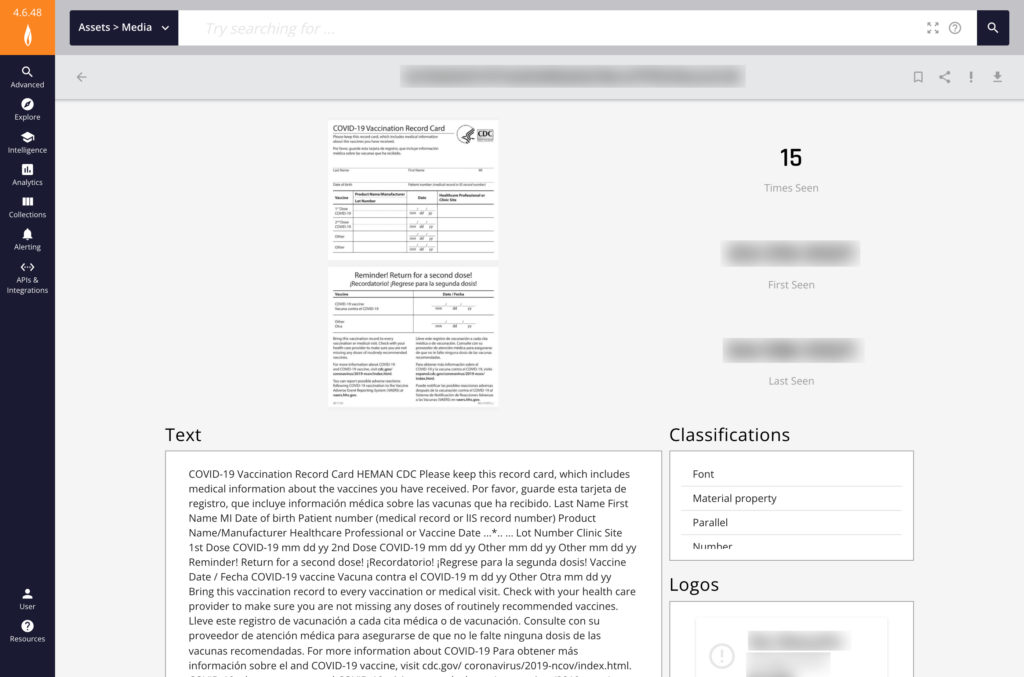
How do Threat Actors Use Images for Risk Exposure?
Threat actors are increasingly showcasing sensitive information on chat platforms, including compromised bank accounts, domains, usernames, passwords, networks, devices, phone numbers, stolen identities, exploit code, as well as Remote Desktop Protocol (RDP) access.
Furthermore, threat actors may use images to boast about their recent activities, share sensitive or exploitative information, and even plan future attacks.
As image-rich, mobile-first communication becomes a primary mode of communication in illicit communities, organizations across the public and private sectors require insight into how these threat actors gain access to—then leverage—sensitive information.
While posting images may lend legitimacy to threat actors’ claims, it also provides valuable information for security teams to discover and take appropriate action.
Understanding the Criminal Mindset Behind Image Sharing
Let’s pretend for a moment you’re in the market to purchase stolen credentials to a bank account. To accomplish this, you scan through multiple text-based posts on an illicit channel (chat server, e.g.); each poster claims to have access to various types of banking and investment account data.
How do threat actors on the buy side verify that the sellers actually have access to financial accounts? On the other hand, how do these sellers provide proof to potential buyers that the stolen credentials are viable?
Finally, if you’re a member of a fraud team that’s diligently hunting for indicators of compromise (IOCs), how would you also determine which claims are credible (or false positives) and therefore require action.
The answer? Images provide proof.
Related reading: From Ransomware to DDoS: Guide to Cyber Threat Actors—How, Why, and Who They Choose to Attack
What are the Best Use Cases for OCR in Security?
Security teams can leverage OCR technology to discover and be alerted when activities are taking place that could pose a potential threat to their business and customers. Now, let’s take a look at a few real life use cases to better understand how this can occur.
OCR, Fraud, and Compromised Credentials
Fraud teams at banks and other financial institutions have certainly had their hands full. The amount of threats and their level of sophistication has been steadily on the rise, with a 149% increase in digital fraud this year alone. Fraudulent purchases and compromised accounts cost banks billions annually, making fraud mitigation a primary goal.
This poses a huge challenge to fraud teams to not only know which illicit communities to monitor across the deep and dark web, but also to sift through the massive amounts of data in order to identify relevant threats to their business and customers, such as credit card fraud made possible by stolen credentials. OCR technology can be a game changer in helping to overcome this challenge.
When pointed toward a robust dataset of illicit online communities, OCR capabilities allow fraud teams to search through not only text chatter, but also images posted by threat actors, such as a company logo on a customer statement that has fallen into the wrong hands.

Detecting Internal and Insider Threats with OCR
It’s essential for CTI and SOC teams to gain a stereoscopic understanding of potential vulnerabilities, including risk apertures opened by internal actors. These data leaks can be caused by honest mistakes, such as inadvertently storing code in open repositories, or by insiders with malicious intent who seek to profit off of their access to sensitive information.
OCR allows security teams to detect when this activity occurs. By searching images for company names/logos, a security analyst can identify images the insider has posted as proof of access, for example. This could be in the form of an employee badge, or possibly a screenshot of a system or application of interest.
Practical Applications of OCR for Physical Security
It isn’t only cyber and application security teams that can benefit from OCR search technology. While maybe not quite as apparent, physical security teams can enjoy the benefits of this capability as well.
As in the insider threat example above, an employee offering a picture of his/her badge as proof of physical access can be caught with OCR. Additionally, bad actors might also post pictures of building entrances that might include the company’s name/logo. Keypads, scanners, and other physical security devices may have known exploits that could allow unauthorized access to company facilities.
Using OCR search capabilities to search for your company’s physical security devices that are in use could help your security department discover and take action against these types of risks.
What are Other Important Applications of OCR?
There are many other use cases OCR can help address for security and fraud teams, in addition to the few mentioned above.
- Identity theft: OCR helps find photos of fake IDs, such as licenses and passports.
- Compromised accounts: It finds images that show access to stolen bank or social media accounts.
- Mail fraud: It helps find photos of fake checks.
- Physical safety: It finds images that show where businesses or customers are located. This helps prevent harm.
- Illegal drug trade: It finds fake medical notes used to get drugs illegally.
- Crypto wallets: It can see if the keys to a digital wallet are shown online.
Real World Examples of ROI from OCR Technology
Flashpoint customers have found immense value leveraging our OCR capabilities to identify potential risks to their organizations.
- A financial services customer identified $10.1M in at-risk account balances and secured the accounts within six days of Flashpoint’s launch of OCR capabilities.
- A financial services customer identified an average of 125 account screenshots with $6M at risk on a monthly basis.
- Multiple gaming industry customers have found OCR searches helpful to identify new types of “cheats” targeting their platforms.
- A Flashpoint customer identified an image within Flashpoint’s collections showcasing a tutorial targeting a state’s unemployment insurance site. Flashpoint’s OCR capability identified the image as the step-by-step example for how to claim unemployment, which mentioned the customer’s corporate name as the employer in one of the steps.
See Flashpoint’s OCR Solution in Action
Organizations across a variety of sectors, from financial institutions to governments and law enforcement, leverage Flashpoint’s OCR technology to proactively identify threats, prevent fraud, and take action to combat exposure to risk. To see our OCR technology in action and learn how it can help your organization, request a demo or sign up for a free 90-day trial today.

OCR Frequently Asked Questions (FAQs)
Q: How is Flashpoint’s OCR solution used in cybersecurity to identify risks?
A: OCR (Optical Character Recognition) is a technology that identifies and extracts text, logos, and specific objects from images. In a cybersecurity context, it allows security teams to monitor illicit communities—such as dark web forums and chat apps—to find sensitive data that threat actors share as images to avoid simple text-based detection.
| Key Capability | Security Application |
| Text Extraction | Finding usernames, passwords, or bank account numbers within screenshots. |
| Logo Detection | Identifying when a company’s official branding appears on a fraudulent document. |
| Object Recognition | Detecting physical security hardware, like badges or keypads, in photos. |
Q: How does machine learning improve the effectiveness of Flashpoint’s OCR?
A: Machine learning enhances OCR by allowing the system to inspect and classify images with high speed and accuracy. It eliminates the gap between raw data and actionable intelligence by making images immediately searchable. Advanced machine learning models can even interpret text that is curved, diagonal, or written in multiple different languages.
- Context: Classifies the type of image (e.g., a credit card vs. a passport) automatically.
- Speed: Processes massive image datasets in seconds.
- Searchability: Turns unsearchable “dead” pixels into live, indexed text.
Q: What is the ROI of using OCR for fraud prevention?
A: The return on investment (ROI) for OCR is measured by the rapid identification and securing of at-risk financial assets. By catching compromised account details as soon as they are posted in the underground, organizations can prevent millions of dollars in losses before the fraud actually occurs.
| Industry | Real-World ROI Example |
| Financial Services | One firm identified $10.1M in at-risk balances within six days of use. |
| Banking | A customer flags $6M in at-risk account screenshots every month. |
| Public Sector | Detected step-by-step tutorials using a company’s name for UI fraud. |

